Burglar Alarm Circuits
1. Purpose and Functionality
1.1 Purpose and Functionality
Burglar alarm circuits serve a crucial role in the contemporary landscape of security systems. Their primary purpose is to detect unauthorized intrusions, thereby safeguarding properties and individuals. These circuits utilize a range of sensors and components to monitor environments continuously and provide alerts when security breaches occur. By analyzing the mechanisms through which these systems operate, we can gain valuable insights into their functionality and applications.
Detection Mechanisms
The core functionality of burglar alarm circuits often revolves around various detection mechanisms, which can be categorized based on the principle they operate on. Common detection methods include:
- Passive Infrared (PIR) Sensors: These sensors detect changes in infrared radiation, signaling a presence through body heat. They are particularly effective for indoor applications.
- Magnetic Contacts: Widely used on doors and windows, these sensors activate an alarm when the contact is broken, indicating a potential intrusion.
- Motion Detectors: Utilizing ultrasonic or microwave technologies, these devices can monitor movement in a designated area and trigger alarms accordingly.
- Vibration Sensors: Designed to detect physical disturbances, these sensors are often used in conjunction with secure objects such as safes or windows.
Each sensor type offers its distinct advantages and is selected based on the specific security needs of a space. The integration of these components into an electrical circuit forms the backbone of a burglar alarm system.
Signal Processing and Alarm Activation
Once a sensor detects an intrusion, the next critical step involves signal processing. Typically, this is accomplished through microcontrollers or dedicated alarm modules that receive the input signals from sensors.
The processing unit often employs threshold-based algorithms to evaluate the sensor data. For example, if a PIR sensor detects infrared radiation beyond a pre-defined threshold, the system recognizes it as valid motion. A mathematical representation of this principle can be defined as follows:
In this equation, \(S(t)\) represents the system's signal output at time \(t\), \(IR(t)\) indicates the detected infrared level, and \(T\) is the established threshold value. Upon confirming an intrusion, the circuit activates alarm mechanisms which can include audible sirens, notifications to mobile devices, or other alert methods.
Real-world Applications
To contextualize the functionality of burglar alarm circuits, consider their practical applications across various sectors:
- Residential Security: Homeowners frequently install alarm systems to protect their properties and create a deterrent against potential burglars.
- Commercial Premises: Businesses employ these circuits to prevent theft, particularly in warehouses, retail stores, and office environments.
- Industrial Facilities: Manufacturing plants and infrastructure sites utilize advanced alarm circuits integrated with access control to protect sensitive operations.
- Smart Homes: Increasing integration of burglar alarms with IoT devices enhances security through automated monitoring and remote control capabilities.
Overall, the design and functionality of burglar alarm circuits have evolved significantly, primarily driven by advancements in sensor technologies and microcontroller capabilities. Their importance in enhancing security and deterring crime cannot be overstated, reflecting ongoing innovations in the field.
1.2 Types of Burglar Alarm Systems
The design of burglar alarm systems can be classified into various types based on operational principles, sensor technology, and integration capabilities. Each type serves a specific purpose and is tailored for different security needs. Understanding these entails grasping underlying technologies, identifying practical applications, and evaluating their effectiveness.
Wired Burglar Alarm Systems
Wired alarm systems utilize physical cables to connect sensors and alarm panels. These systems offer several advantages, including reliability and reduced vulnerability to wireless signal interference. However, installation can be labor-intensive due to the need to run wires through walls and ceilings.
Key components of wired systems include:
- Control Panel: Acts as the central hub, receiving signals from sensors and managing alarms.
- Wired Sensors: Typically employs magnetic contacts, motion detectors, and glass break detectors connected via cable.
- Sound Alarm Devices: Alarms, typically sirens or bells, are activated when unauthorized access is detected.
The use of shielded twisted pair cables can improve signal quality and reduce electromagnetic interference, which is critical in environments with numerous electronic devices.
Wireless Burglar Alarm Systems
Advancements in wireless technology have spurred the growth of wireless alarm systems, which offer flexibility and ease of installation. Unlike wired systems, these use radio frequency (RF) communication to transmit signals.
The main components of wireless systems consist of:
- Control Panel: Similar to wired systems, but equipped with RF receivers.
- Wireless Sensors: Include passive infrared (PIR) motion detectors, door/window contacts, and image capture cameras.
- Power Supply: Often involves batteries, promoting easy placement but necessitating periodic maintenance.
Wireless alarm systems can swiftly integrate with smart home devices, enhancing remote monitoring capabilities. However, security vulnerabilities to jamming attacks and possible interference are important to consider.
Monitored vs. Unmonitored Systems
Another means of classifying burglar alarm systems is based on their monitoring capabilities. Monitored systems are actively supervised by security companies, providing immediate notification to authorities upon an alarm trigger. This adds a layer of security;
- Monitored Alarm Systems: Ideal for businesses or residences requiring constant oversight. These systems generally include a subscription fee for 24/7 monitoring service.
- Unmonitored Alarm Systems: Often less expensive, these systems alert property owners or designated contacts. However, there's a reliance on user response times to address potential breaches.
Smart Burglar Alarm Systems
In recent years, the integration of the Internet of Things (IoT) has led to the development of smart burglar alarm systems. These advanced systems use Wi-Fi or mobile networks to facilitate communication between devices, allowing users to control their alarm systems via mobile applications.
Features often found in smart systems include:
- Remote arming/disarming capabilities
- Real-time alerts via smartphone notifications
- Integration with home automation systems for cohesive security solutions
Smart systems improve user convenience and provide insights into security status through data analysis and real-time monitoring. Nevertheless, dependence on network connectivity raises potential cybersecurity concerns that must be managed carefully.
Conclusion
The choice of burglar alarm system depends heavily on user requirements, environmental factors, and the desired level of security. With advances in technology, the market is expanding, offering varied solutions tailored to specific security needs. Moving forward, understanding the intricacies of these systems involves continuous research into emerging technologies, including connectivity, integration, and security enhancements.
2. Sensors: Types and Uses
2.1 Sensors: Types and Uses
In burglar alarm circuits, sensors play a critical role as the frontline elements that detect unauthorized entry or suspicious activity. Their efficacy determines the reliability of the security system as a whole. The various types of sensors utilized in these circuits not only differ in their operational principles but also have distinct applications based on the specific requirements of the environment they monitor.Types of Sensors
The two primary categories of sensors used in burglar alarm circuits are contact sensors and passive sensors, each with several subtypes offering varied functionalities.Contact Sensors
Contact sensors, often referred to as magnetic sensors or switch sensors, are typically employed on doors and windows. They consist of two main components: a magnet and a switch. When the door or window is closed, the magnet keeps the switch activated; however, upon opening, the magnetic field is interrupted, triggering an alarm.- Magnetic Reed Switches: These utilize a reed switch, which closes in the presence of a magnetic field, making them ideal for unobtrusive installations.
- Micro Switches: Mechanical switches that activate when the physical pressure is applied; they are commonly used in more robust applications.
Passive Infrared Sensors (PIR)
Passive Infrared (PIR) sensors detect the infrared radiation emitted by living beings. When a person moves through the sensor’s detection area, the change in heat levels is interpreted as motion. This type of sensor effectively minimizes false alarms by ignoring static objects and is commonly utilized for large open areas.Ultrasonic Sensors
Ultrasonic sensors operate by emitting sound waves at frequencies above the audible range. They measure the reflection of these waves off moving objects to detect intruders. Unlike PIR sensors, ultrasonic sensors are less sensitive to heat signatures, allowing them to detect motion without relying solely on thermal variations.Laser Sensors
Laser sensors employ a focused beam of light to create an invisible security barrier. When the beam is interrupted, it triggers an alarm. This technology is particularly advantageous for outdoor applications where visibility and environmental adaptability are paramount.Applications and Practical Relevance
The choice of sensor in a burglar alarm circuit depends significantly on the specific requirements of the environment: - Indoor Environments: Contact sensors and PIR sensors are prevalent indoors due to their unobtrusive nature and ability to cover entry points effectively. - Outdoor Environments: Ultrasonic and laser sensors are more suitable for outdoor settings, where wind or animals could trigger false alarms in traditional contact sensors. In commercial settings, often a combination of different sensors is used to create a layered defense. This not only enhances security but also provides redundancy in case one sensor type fails. Additionally, advancements in sensor technology, such as the integration of IoT capabilities or the use of machine learning algorithms to reduce false alarm rates, are becoming more common. These innovations allow for more intelligent and feature-rich security systems that adapt to an environment's specific needs. In conclusion, understanding the myriad types of sensors available and their respective applications enables engineers and security professionals to design more effective burglar alarm systems. Tailoring sensor selection to the particular needs of a property enhances security and ultimately creates a more resilient environment against intrusions.2.2 Control Panels: Function and Operation
In the intricate landscape of burglar alarm systems, control panels stand as the nerve center, orchestrating the interaction among various components and responding to stimuli from sensors and user interfaces. This subsection delves deeply into the multifaceted function and operation of control panels, exploring their essential role in alarm systems, their design considerations, and their integration with advanced technologies.
Functionality of Control Panels
Control panels serve multiple critical functions within a burglar alarm system:
- Central Processing Unit: It interprets signals received from sensors, deciding whether an alarm should be triggered based on predefined conditions.
- User Interface: Control panels usually feature keypads or touchscreens that allow users to arm or disarm the system and manage settings.
- Communication: They facilitate communication with external monitoring stations and mobile devices to ensure alerts are sent in real-time.
- Power Management: Control panels often include backup power systems to maintain operation during power outages, typically utilizing rechargeable batteries.
Components of Control Panels
A typical control panel comprises several core components, each playing a vital role:
- Microcontroller or Microprocessor: Acts as the brain of the system, processing input signals and executing commands based on programmed logic.
- Input/Output Interfaces: These connections exist for both wired and wireless sensors, as well as for user input devices and communication outputs.
- Memory: Control panels often have both volatile and non-volatile memory, storing configuration settings and event logs.
- Communication Modules: Depending on the system design, these may include cellular, Wi-Fi, or Ethernet modules for connectivity with monitoring services.
Operational Mechanism
The operational flow begins when a sensor, triggered by an intrusion or defined parameter (like motion or broken glass), sends an input signal to the control panel. The microcontroller processes this input and applies programmed rules to determine if the alarm should activate. When an alarm state is initiated, the control panel can:
- Activate local audible and visual alarms, such as sirens and strobe lights.
- Send notifications to the user through SMS, email, or mobile apps.
- Forward alerts to a monitoring station for professional intervention.
Moreover, control panels are equipped with features that enable them to recover from errors or resets, enhancing their resilience against potential security breaches.
Integration with Smart Technologies
With the rise of smart home technology, modern burglar alarm systems increasingly feature integration capabilities. Control panels now often support:
- IoT Connectivity: Allowing interconnected devices to communicate and respond to each other, improving overall security measures.
- Remote Monitoring: Users can access their alarm systems via mobile applications, controlling and monitoring their security from anywhere.
- Automation Features: Integration with other home systems (like lighting) can create automated responses to potential breaches, such as lighting up the area when motion is detected.
This evolution in control panel design illustrates the shift towards enhanced security solutions that are not only reactive but also proactive, leveraging technology to create a safer living environment.
Conclusion
Control panels are crucial in the realm of burglar alarm systems, bridging the gap between user needs and complex technology. As alarm systems evolve alongside consumer technology, the functionality and operational design of control panels will undoubtedly continue to adapt, leading to more secure systems equipped for the demands of the modern world.
2.3 Alarm Devices: Sirens and Notifications
In the realm of burglar alarm systems, the integration of alarm devices such as sirens and notification systems plays a pivotal role in deterrent effectiveness and response activation. By understanding these systems, one can appreciate how they not only alert occupants and authorities but also serve as psychological deterrents against potential intruders. Let's dive deeper into the operational mechanics and applications of sirens and notification systems.
Fundamentals of Siren Operation
At their core, sirens utilize the principles of acoustics to generate sound waves that can alert individuals over a significant distance. Sound is a mechanical wave that propagates through a medium, typically air, and is characterized by its frequency and amplitude. In alarm systems, sirens are designed to emit sound at specific frequency ranges that are not only audible but are also effective in attracting attention.
Most commercial sirens operate in the frequency range of 1 kHz to 5 kHz, which is optimal for penetrating ambient noise and ensuring that their sound can be perceived above background sounds. The output sound can be generated by various means, including:
- Electromechanical devices, which use motors and mechanical components to produce sound.
- Piezoelectric speakers that use the piezoelectric effect to generate sound through rapid vibrations.
- Compressed air-driven sirens that utilize air pressure to create a loud, piercing sound.
Design Considerations for Sirens
When integrating a siren into a burglar alarm system, several design considerations must be addressed:
- Power Supply: Sirens require a reliable power source, typically supplied by the main system battery or a backup power supply to ensure functionality during power outages.
- Decibel Level: The effectiveness of a siren is largely dictated by its sound pressure level, measured in decibels (dB). Most alarm systems aim for a minimum output of 100 dB at one meter distance for adequate audibility.
- Weather Resistance: For outdoor systems, sirens must be constructed to withstand environmental factors such as rain, wind, and extreme temperatures.
- Strobe Lights: Integrating visual alerts, such as strobe lights, can enhance effectiveness, particularly for areas where a siren may not be heard due to distance or noise.
Notification Systems: Alerts Beyond Sound
While audible alarms are critical, modern burglar alarm systems also encompass notification devices that enhance the response capabilities of the system. These notifications can come in the form of:
- Text Alerts: Systems can be designed to send SMS or email alerts to designated contacts, ensuring that even when occupants are away, they can be informed of security breaches.
- App-based Notifications: With the rise of IoT (Internet of Things), many alarm systems now connect to mobile applications, providing real-time alerts, live feeds, and system diagnostics.
- Monitoring Services: Professional monitoring services can receive alerts directly from the system and will respond by contacting emergency services if necessary.
Practical Implementation
The integration of sirens and notification systems not only enhances the immediate alertness to potential threats but also contributes to the overall security architecture. For instance, smart home systems can combine motion sensors with sirens and automated notifications, creating a robust line of defense. This multilayered approach ensures that the alarm system provides a comprehensive solution for safeguarding premises.
Historically, technologies used for alarm notifications have evolved. From the early pneumatic bells used in security systems to today's sophisticated digital alerts, the constant aim has been to enhance reliability, clarity, and response time.
In this equation, I represents the intensity of sound in decibels, P denotes the power of the siren output, and A is the area over which the sound is distributed. A deep understanding of this relationship is crucial in quantifying the effectiveness of a siren in different environments.
As technology advances, the adaptability and configurability of alarm systems are expected to improve further. The continued focus on integrating cutting-edge notification and alarm technologies will ensure higher efficiency and response rates in real-world scenarios. Through exploring both auditory devices and notification systems, one can gain a holistic view of modern burglar alarm systems and appreciate their critical role in security technology today.
3. Basic Circuit Design Principles
3.1 Basic Circuit Design Principles
In designing burglar alarm circuits, an engineer or researcher must take into account several fundamental circuit design principles that ensure reliability, efficiency, and responsiveness. Understanding these principles lays the groundwork for developing complex alarm systems and enhances the functionality of individual components.Understanding the Components
The basic burglar alarm circuit can be envisioned as an integration of several components. These typically include power supplies, sensors (like motion detectors or door/window sensors), control units (microcontrollers or relay systems), output devices (such as sirens and lights), and communication systems if remote monitoring is involved. Each component serves a critical function:- Power Supply: Provides the necessary voltage and current for the operation of the circuit components.
- Sensors: Detect intrusions by monitoring physical changes such as movement, magnetic field interruptions, or acoustic signals.
- Control Unit: Processes inputs from sensors and determines the appropriate response.
- Output Devices: Trigger alarms or notifications based on control unit decisions.
- Communication Systems: Facilitate remote notifications and interactions, often through cellular or network connections.
Creating Versatile Circuit Designs
A versatile burglar alarm system must be able to function under various scenarios. This entails designing circuits that can adapt to changes in external conditions, or accommodate different types of sensors. For example, a combination of passive infrared sensors (PIR) and magnetic reed switches can create a layered detection strategy, improving security and reducing false alarms. When designing these circuits, it is crucial to apply the principles of series and parallel connections strategically. In a series connection, all components share the same current, while in a parallel connection, components share voltage.- Series Connections: Useful for circuits where all devices must be activated simultaneously. A failure of one component will stop the entire circuit.
- Parallel Connections: Allows each device to operate independently, ensuring that if one sensor fails, the others continue to function, thereby enhancing reliability.
Equations Governing Circuit Behavior
Understanding the mathematical principles governing circuit operation is essential. Applying Ohm's Law, which states that \( V = IR \) (voltage equals current times resistance), can aid in the design of power supply systems to ensure that all components receive the correct voltage. Additionally, analysis of power consumption is critical when designing battery-operated systems. The total power \( P \) consumed can be calculated as:3.2 Schematic Representation of Alarm Circuits
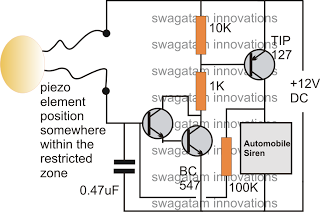
Understanding the schematic representation of burglar alarm circuits is crucial for both the design and troubleshooting phases. These schematics embody the functional arrangement of components, illustrating how different elements interact to provide security within a given environment. In this discussion, we will dissect the fundamental components of alarm circuits and demonstrate their interrelationships through illustrative schematic diagrams.
Basic Components of Alarm Circuits
Burglar alarm circuits consist of a variety of electronic components, each serving a specific purpose. The fundamental elements typically include:
- Power Supply: Provides the necessary voltage and current for the operation of the circuit.
- Sensor: Detects unauthorized entries or disturbances; types include motion detectors, door/window sensors, and glass break detectors.
- Controller: Processes inputs from sensors and determines the response action, often incorporating microcontrollers for advanced functionality.
- Alarm Actuator: Triggers an alert through sirens or notifications when a breach is detected.
- Communication Module: Sends alerts to a monitoring service or the property owner, often through cellular or internet connections.
Each component’s functionality is determined by its electrical properties and the circuit design principles that govern their interactions.
Schematic Design Principles
The design of burglar alarm circuit schematics requires a clear understanding of electronic symbols and their associated meanings. Fundamental symbols include:
- Resistors: Represented by a zigzag line, resistors limit the flow of electric current through the circuit.
- Capacitors: Identified by two parallel lines; capacitors store energy and can filter signals.
- Diodes: Denoted by an arrow with a line; diodes allow current to flow in one direction, often used to protect circuits from damage.
- Integrated Circuits (ICs): Represented by a rectangle; they can perform complex functions in the alarm system.
Properly integrating these components in a schematic requires a methodical approach, beginning with the power supply, followed by the series or parallel arrangement of the sensors and controllers, and concluding with the alarm actuators. This arrangement, whether a series or parallel configuration, determines the overall functionality and reliability of the system.
Illustrative Schematic Example
Below is a simple schematic representation of a basic burglar alarm circuit involving a motion sensor, microcontroller as the controller, and an alarm actuator. This diagram highlights the interconnections and signal flow throughout the system.
This representation allows an advanced reader to interpret the design choices made, analyze the signal pathways, and troubleshoot potential connection issues. Understanding this schematic is paramount when engaging in either enhancing existing systems or developing new security solutions.
Real-World Applications
The understanding of these schematic representations is not merely theoretical; they are directly applicable in designing effective security systems. For instance, enhanced alarm systems currently utilize IoT (Internet of Things) technologies, which require more complex schematic designs to incorporate networked sensors and actuators. Engineers and researchers must prioritize the ability to modify and innovate these designs to address emerging security challenges.
In conclusion, the schematic representation of burglar alarm circuits serves as a fundamental tool in the field of electronics and security engineering. Mastery of these designs facilitates advancements in security technologies and equips engineers to meet contemporary security demands effectively.
3.3 Layout Considerations for Effective Installation
Installing a burglar alarm circuit involves strategic planning of both the physical layout and the component placement. The effectiveness of the alarm system is significantly influenced by these layout considerations, which not only affect the performance and reliability of the circuit but also its overall resilience against intrusions.Strategic Sensor Placement
The performance of a burglar alarm heavily relies on the positioning of its sensors. Passive Infrared Sensors (PIR) are sensitive to heat changes in their environment. They should be placed in locations where they can detect heat signatures from moving bodies but be cautious of direct sunlight or objects that may obstruct the infrared beams. Additionally, an understanding of the sensing range and field of view (FoV) for the sensors will ensure comprehensive coverage of the intended area. Door and Window Contacts must be installed on all accessible entry points. When choosing where to install them, attention should be paid to the likelihood of forced entry and the configuration of the building.Determining Blind Spots
To maximize coverage, it is crucial to identify potential blind spots in the circuit’s design. 1. Conduct a site assessment to evaluate areas that may be unmonitored. 2. Use a signal strength analysis to ensure adequate wireless coverage if the system uses wireless sensors. By ensuring proper spacing and avoiding overlapping coverage areas, false alarms from overlapping sensors that detect the same motion can be minimized.Wiring Considerations
For hardwired systems, the layout of wiring is critical. The choice between running wires along walls versus ceilings, and maintaining appropriate distances from electrical lines to avoid interference, should not be overlooked. Here are some key points: - Wire Length: The total length of wire used can affect the signal integrity. If lengthy runs are necessary, consider using twisted-pair cables to minimize electromagnetic interference (EMI). - Connection Points: Each junction or connection point can be a potential failure point. Using high-quality connectors and ensuring proper insulation can enhance reliability. - Grounding: Install the system with proper grounding techniques to further reduce noise and improve operation. A grounded circuit minimizes the risk of false triggers due to electrical noise.Environmental Factors
Different environmental factors play a vital role in the effectiveness of burglar alarm circuits. This includes: - Temperature Variations: Extreme temperatures can cause components to malfunction. Placing devices in controlled environments where possible, or selecting components that can operate within a broader range, is beneficial. - Moisture and Dust: For outdoor sensors, ensure that they are rated for IP (Ingress Protection) standards to withstand environmental challenges. Moreover, regular maintenance checks can help in cleaning sensors that may have accumulated debris.Integration with Other Security Systems
Consider how the burglar alarm integrates with other security systems like CCTV and fire alarms. Ensuring that these systems can communicate without interference requires careful planning. Installing a central control panel that allows for this communication not only enhances security but also simplifies monitoring and management.Conclusion
In summary, the placement of sensors, the management of wiring, consideration for environmental factors, and integration with other security systems are all crucial layout considerations for effective installation of burglar alarm circuits. Engaging in thoughtful and informed planning ensures that the burglar alarm system provides optimal protection, deterring potential intruders while minimizing false alarms. Implementing these considerations will lead to a robust alarm system capable of safeguarding valuable assets. Given this overview, the next steps involve hands-on implementation and testing, which will further demonstrate the effectiveness of these layout strategies in real-world scenarios.4. Diagnosing Sensor Failures
4.1 Diagnosing Sensor Failures
In the realm of burglar alarm circuits, the reliability of sensors is paramount. These sensors form the first line of defense in security systems, detecting unauthorized entries and triggering alarms. However, their effectiveness can be compromised due to various factors, including mechanical wear, environmental conditions, and electronic malfunctions. Understanding how to diagnose sensor failures is crucial for maintaining system integrity and ensuring prompt responses to security breaches.Understanding Sensor Types and Their Vulnerabilities
Burglar alarms utilize several sensor types, including passive infrared (PIR), magnetic contact sensors, vibration sensors, and photoelectric sensors. Each type operates on different principles and is vulnerable to distinct failure modes:- Passive Infrared (PIR) Sensors: These sensors detect motion by sensing changes in infrared radiation. Failure may occur due to aging, dirt accumulation on lenses, or changes in the ambient environment.
- Magnetic Contact Sensors: Common in door and window alarm systems, these sensors can fail due to misalignment or mechanical wear in the magnetic reed switch.
- Vibration Sensors: These sensors detect disturbances indicating forced entry. They are sensitive to installation conditions and may fail if not securely mounted.
- Photoelectric Sensors: Typically used in outdoor applications, these sensors can become obstructed by environmental debris, leading to false alarms or missed detections.
Common Symptoms of Sensor Failures
When diagnosing sensor failures, it is critical to look for observable symptoms, which can include:- No response to stimuli: This implies a complete failure of the sensor.
- Frequent false alarms: Indicates possible electrical interference or malfunction.
- Delayed response times: Suggests potential sensor aging or degradation.
- Physical damage: Visual inspection of the sensor hardware may reveal obvious faults.
Step-by-Step Diagnostic Process
Diagnosing sensor failure effectively requires a systematic approach: 1. Conduct a Physical Inspection: Examine each sensor for signs of physical damage, dirt, or misalignment. Check for loose connections in all wiring and ensure that mounting hardware is secure. 2. Test the Signal: Use a multimeter to check for continuity in wired sensors or to test for voltage outputs in active sensors. For instance, applying a heat source to a PIR sensor can reveal whether it responds correctly to motion detection. 3. Environmental Conditions: Assess the operational environment. Extreme temperatures, moisture, or electromagnetic interference may affect sensor performance. 4. Replace and Retest: If no physical issues are found but the sensor remains unresponsive, replace it with a known good unit and monitor reactions to stimuli. This test will confirm whether the issue lies with the sensor or surrounding circuitry.Advanced Techniques for Diagnosing Sensor Failures
For advanced practitioners, leveraging technology can enhance diagnostic capabilities: - Oscilloscope Use: An oscilloscope can be employed to analyze the sensor’s output signal over time. This is particularly useful for identifying intermittent failures that may not present themselves during manual tests. - Signal Processing Techniques: Implement signal processing algorithms to filter noise from the sensor outputs, enhancing the ability to detect legitimate signals amidst interference. - Data Logging: In complex systems, manage continuous data logging of sensor outputs to correlate sensor behavior over time, facilitating the identification of patterns indicative of failure. By employing these techniques, engineers and technicians can derive insights far beyond basic operational checks, establishing a comprehensive understanding of each sensor's health.Real-World Applications in Security Systems
The practical implications of successfully diagnosing sensor failures extend to effective security system management. Organizations can minimize downtime from false alarms and ensure that preventive measures remain functional. For example, in the retail sector, maintaining operational sensor systems can directly impact loss prevention strategies, while in residential applications, users gain peace of mind knowing their systems respond reliably. Thus, thorough knowledge and strategic approaches towards diagnosing sensor failures not only enhance individual system reliability but also contribute to the overarching security framework, leading to safer environments for both individuals and businesses.4.2 Control Panel Issues
The control panel in a burglar alarm system serves as its operational heart, integrating inputs from various sensors and generating corresponding outputs that dictate the system's behavior. Understanding potential issues within this critical component can significantly enhance the reliability and effectiveness of the overall alarm system. One major challenge in maintaining optimal functionality of control panels is their susceptibility to environmental factors. For instance, exposure to extreme temperatures or humidity can affect the performance of electronic components, leading to malfunctioning or false alarms. This phenomenon is particularly pronounced in thermistors, which can change resistance with temperature fluctuations, causing erratic sensing behavior. In addition to environmental concerns, electrical issues such as noise interference can disrupt the functionality of the control panel. Noise can stem from various sources, including adjacent electrical components and external radiating devices. Implementing shielding techniques or employing differential signaling can mitigate these issues, ensuring that the system retains signal integrity. Moreover, software glitches in the control panel's firmware can also pose significant challenges. These glitches may arise from coding oversights or unforeseen interactions between the control panel and peripheral devices. Robust testing protocols can aid in identifying such faults prior to deployment. For effective troubleshooting, it is essential to establish a baseline performance metric for the control panel. Regular diagnostic checks can be implemented to monitor the health of the system. These checks may include testing voltage levels at various nodes within the circuit, confirming the operational status of alarm triggers, and assessing the responsiveness of user interfaces. One critical metric in evaluating a burglar alarm control panel is its response time. The response time can be defined as the duration taken by the system to react to a triggered sensor and activate the alarm. A quick response time is vital to maximizing deterrence and minimizing potential losses. The effectiveness of response time can be quantitatively assessed using the formula:References and Further Reading
- Understanding Control Panels in Alarm Systems — This article offers an in-depth analysis of how control panels work in alarm systems, detailing various designs and implementations.
- Burglar Alarm System Seminar — A comprehensive overview of burglar alarm systems, including technical specifications, functionality, and control panel issues.
- Signal Integrity in Security Systems — A research paper discussing noise issues in security systems and proposed solutions for maintaining signal integrity.
- Designing a Burglar Alarm System — This resource outlines the fundamental principles and considerations in designing effective burglar alarm systems.
- Noise Reduction Techniques in Electronics — An article dedicated to various strategies for minimizing noise in electronic circuits, which is crucial for alarm systems.
- Firmware Errors in Burglar Alarm Systems — A paper exploring the impact of firmware errors on burglar alarm systems and methodologies for improving reliability.
- The Role of Alarm Response Time in Effective Security — This article examines the critical importance of alarm response time and how it affects overall security effectiveness.
4.3 Signal Interference and Solutions
Burglar alarm circuits are crucial for enhancing security, yet these systems can face challenges due to signal interference, which may hinder their performance. Understanding the nature of these interferences and implementing effective solutions is vital for the reliability of such security systems.Understanding Signal Interference
Signal interference in burglar alarm circuits can be categorized into several types: electromagnetic interference (EMI), radio frequency interference (RFI), and environmental noise. EMI generally originates from various electronic devices, while RFI is specifically associated with communication signals, like those from radios or cellular devices. Environmental noise may arise from natural phenomena or mechanical systems. The performance of alarm systems is critically impacted by these interferences, potentially leading to false alarms or, conversely, an inability to detect actual intrusions. This can be particularly detrimental in security applications, where reliability is key.Mathematical Modeling of Signal Interference
To better understand and quantify the impact of signal interference on burglar alarm systems, we can model the signal-to-noise ratio (SNR), a key factor that determines the quality of the received signal. The SNR can be expressed mathematically as: $$ SNR = \frac{P_s}{P_n} $$ where: - \( P_s \) is the power of the signal, - \( P_n \) is the power of the noise. In practical applications, this equation serves as a basis for evaluating whether a specific security system is capable of effectively discriminating between relevant signals and interference.Assessing Interference Sources
Identifying the primary sources of interference is essential for mitigation. Conducting a spectrum analysis can help in understanding which frequencies are affected and how severe the interference is. Tools such as a spectrum analyzer can visually represent the power spectrum of signals, allowing engineers to pinpoint where the most significant disruptions are occurring.Solutions to Mitigate Signal Interference
Addressing signal interference requires a multi-faceted approach. Here are several strategies that can enhance the robustness of burglar alarm circuits:- Shielding: Employing physical barriers to block EMI can significantly reduce interference. Materials such as copper or aluminum are effective for creating shields around sensitive components.
- Differential Signaling: Utilizing differential signaling techniques, where two complementary signals are sent, can help improve immunity to common-mode noise. This is particularly effective over longer transmission distances.
- Error Correction Algorithms: Implementing algorithms that can detect and correct errors in transmitted signals can enhance the resilience of alarm systems against interference. These methods increase the reliability of signal interpretation.
- Frequency Hopping: This technique involves rapidly switching frequencies during transmission. By utilizing multiple frequency channels in a predefined sequence, it becomes less likely for interfering signals to disrupt the communication.
- Filtering: Incorporating filters to eliminate unwanted frequencies can strengthen the SNR. High-pass or low-pass filters can be selected based on the specific application needs of the alarm system.
Real-World Applications
In practical deployments, systems designed with these mitigation techniques have shown improved performance. For instance, commercial intruder alarm systems often include built-in filtering and differential signaling to ensure that they are not falsely triggered by environmental noise or electronic devices nearby. In conclusion, recognizing and addressing the multifaceted nature of signal interference in burglar alarm circuits is essential for the advancement and reliability of security technologies. Through rigorous analysis and strategic implementation of solutions, alarm systems can be optimized for real-world conditions and maintain their integrity as a critical component of security infrastructure.5. Wireless vs. Wired Alarm Systems
5.1 Wireless vs. Wired Alarm Systems
The discussion of burglar alarm circuits inevitably involves comparing wireless and wired systems. Each type of alarm system presents unique advantages and disadvantages, influencing their application in both residential and commercial settings. Understanding the underlying principles and practical implications of both technologies is crucial for advanced practitioners in electronics and security systems.Understanding Wired Alarm Systems
Wired alarm systems operate using a well-established network of physical wires connecting all components, including sensors, control panels, and alarm notifications. This traditional approach has several inherent advantages, namely reliability and security. Reliability stems from the stability of wired connections, which eliminate common issues like signal interference and range limitations encountered in wireless systems. This makes wired systems particularly effective in environments with substantial electromagnetic interference, such as industrial settings. Additionally, security is enhanced, as hard-wired systems are less vulnerable to hacking or unauthorized interception compared to wireless signals, thus providing robust protection against potential breaches. However, wired systems also present challenges. Installation can be labor-intensive, requiring extensive planning to lay down the wiring, which can be cumbersome in preexisting structures. Moreover, the physical limitations of wiring can impose restrictions on system flexibility and scalability.Exploring Wireless Alarm Systems
In contrast, wireless alarm systems utilize radio frequencies to communicate between components. This approach enables a high degree of flexibility in installation, allowing devices to be placed in optimal locations without the constraints of wiring. It is particularly advantageous for temporary setups or buildings where retrofitting with wires is not feasible. The installation process is often quicker and less invasive, which directly reduces costs and disruption. Furthermore, modern wireless technologies, such as mesh networking and advanced encryption protocols, have drastically improved the reliability and security of these systems, mitigating earlier vulnerabilities related to signal interception. However, the inherent nature of wireless systems does mean that they can be subject to limitations involving range and interference. Various factors, including walls, interference from other electronic devices, and environmental conditions, can impact performance. Additionally, battery life becomes a crucial consideration—wireless sensors require periodic replacement or charging, introducing potential service gaps.Practical Applications and Considerations
The choice between wired and wireless alarm systems must be dictated by specific application requirements. For instance, a large industrial site might benefit more from a wired system's durability and reliability, while a residential environment could leverage the flexibility of wireless technology. When deciding between the two, one should consider factors such as:- Installation Environment: Complex structures may be more suited for wireless systems.
- Scalability: Future expansion plans could favor wireless systems.
- Budget: Initial and long-term maintenance costs must be analyzed.
- Security Needs: Analyze susceptibility to physical tampering.
5.2 Integration with Smart Home Technologies
The evolution of burglar alarm circuits has transcended the basic principles of electronics, entering the realm of smart home technologies. This integration not only enhances security but also offers unprecedented control and monitoring capabilities, leveraging advanced communication protocols and networking technologies.
Understanding Smart Home Ecosystems
Smart home technology encompasses a variety of devices interconnected through the Internet of Things (IoT), enabling automation and remote control of home systems. Such devices often include smart locks, surveillance cameras, motion detectors, and environmental sensors, all of which communicate through secure networks. The significance of this system lies in its ability to provide real-time alerts and data to users via smartphones or virtual assistants.
Protocol and Communication Standards
When integrating burglar alarm circuits with smart home systems, compatibility of communication protocols plays a crucial role. Commonly used standards include:
- Wi-Fi: Provides high data rates and ease of integration with existing home networks. However, it requires power and can drain batteries in wireless sensors.
- Zigbee and Z-Wave: Low-power mesh networking protocols designed for IoT devices. These protocols enable direct device-to-device communication, enhancing the responsiveness and reliability of control systems.
- Bluetooth LE: Useful for short-range communications, it is ideal for applications requiring low energy consumption.
Choosing the right protocol depends on factors like range, energy efficiency, and ease of integration with other devices in the smart home ecosystem.
Architectural Design of Integrated Systems
In designing an integrated burglar alarm circuit with smart technology, several core components must be considered:
- Sensor Nodes: These include motion detectors, door/window contacts, and glass-break sensors. Each sensor must be designed to communicate its state effectively in real time.
- Central Hub: This entity communicates with the sensors, aggregates data, and relays information to the user interface. It may utilize a local processing unit or cloud computing for data analytics.
- User Interface: Often realized through mobile applications or web interfaces that allow users to monitor, control, and receive notifications regarding their security status.
The architecture facilitates a two-way communication pathway, allowing not only for alerts in response to potential breaches but also for active monitoring through video feeds or logs.
Practical Applications and Case Studies
The practicality of integrating burglar alarm circuits with smart home technologies can be illustrated through real-world applications:
- Remote Monitoring: A homeowner can monitor their premises in real-time via a smartphone app. If a breach occurs, the app sends immediate alerts, allowing for quick response.
- Geofencing: Some systems leverage GPS data to trigger the alarm status based on the homeowner's geographical location. When users leave a designated area, the system automatically arms itself.
- Automated Responses: Integrated systems may trigger additional safety measures. For instance, if a camera detects an intruder, the system could automatically lock all doors or activate floodlights.
These capabilities not only heighten security but also offer users convenience and peace of mind, underscoring the importance of integrating burglar alarm circuits within the broader scope of smart home technologies.
Future Trends and Considerations
As smart home technologies continue to evolve, we anticipate the emergence of even more sophisticated burglar alarm systems. Trends such as the adoption of artificial intelligence (AI) for predictive analytics and enhanced machine learning algorithms promise to improve false alarm rates by discerning normal household activities from potential threats.
Moreover, considerations regarding privacy, ethical data usage, and secure communication will dictate the framework of future integrations. Engineers and developers must prioritize these elements to ensure that as systems become smarter, they remain trustworthy and secure.
5.3 Mobile Notifications and Remote Access
The integration of mobile notifications and remote access into burglar alarm circuits represents a significant advancement in security technology. These features enable the user to monitor their premises in real-time, receive alerts, and control the alarm system remotely, ultimately enhancing the effectiveness and responsiveness of security measures.
Highly integrated alarm systems often leverage wireless communication protocols, such as Wi-Fi and Bluetooth, or utilize cellular networks to maintain a continuous connection between the alarm system and the user’s mobile device. This connectivity allows for immediate notifications about unauthorized access, system malfunctions, or even environmental alerts like smoke or carbon monoxide detection.
Mobile Notifications
In modern burglar alarm systems, mobile notifications play a critical role. These alerts are typically generated using a series of sensors and microcontrollers, which continuously monitor for unusual activities. Upon detecting a breach, the system can send push notifications to a user’s smartphone or tablet via a dedicated application. The notification mechanism can involve various technologies, including:
- Push Notifications: Utilized by dedicated apps to inform users instantly of any detected security breaches.
- SMS Alerts: A traditional method where system firmware can send alerts via text message.
- Email Notifications: Useful for providing comprehensive activity logs and incident reports.
To ensure reliability, it is critical to design the system with failover mechanisms. For instance, if the primary communication method fails, the system should automatically switch to an alternate method (like SMS) without user intervention.
Remote Access
Remote access opens up a broader realm of capabilities for users. With secure server-client architecture, users can remotely access their alarm systems from anywhere in the world. This functionality typically provides the following features:
- System Control: Users can arm, disarm, or configure settings of their alarm systems remotely through an intuitive interface.
- Real-time Monitoring: Integrating video surveillance allows users to view live feeds directly from their mobile devices.
- System Configuration: Users can receive and configure alerts for different types of alarms or adjust settings based on preferences.
Utilizing secure communication protocols, such as HTTPS or MQTT, is essential to protect user data and maintain privacy. Additionally, implementing two-factor authentication (2FA) adds an extra layer of security, ensuring that remote access is limited to authorized users only.
Real-world Applications
The importance of mobile notifications and remote access in burglar alarm circuits cannot be overstated. For instance, commercial settings such as retail stores often employ such systems to safeguard physical assets. In a case study conducted by a leading security provider, a retail chain that implemented a remote-access alarm system reported a 30% reduction in theft incidents over the course of a year.
For residential users, mobile notifications not only provide peace of mind but enhance the overall user experience by enabling homeowners to respond quickly to incidents. The ability to monitor their home while on vacation or at work has been shown to significantly reduce the anxiety associated with burglary threats.
In conclusion, the incorporation of mobile notifications and remote access in burglar alarm circuits not only maximizes security but also transforms how individuals interact with their safety systems. With ongoing advancements in technology, such features will continue to evolve, providing even greater control and convenience.
6. Planning the Installation Process
6.1 Planning the Installation Process
Planning the installation process of a burglar alarm circuit is vital for ensuring not only effectiveness but also reliability and efficiency of the security system. The first step involves understanding the specific requirements of the installation site, including potential vulnerabilities and environmental factors that may affect the system’s performance. This requires a systematic approach to assessing both the physical and electrical aspects of the installation environment.
Understanding Site Requirements
Before installation, consider factors like the following:
- Building Layout: Analyze the architectural design, identifying entry points and vulnerable areas.
- Environmental Factors: Assess climatic conditions such as humidity, temperature, and possible exposure to vandalism.
- Electrical Infrastructure: Determine the availability of power sources and the configuration of existing circuitry.
By evaluating these elements, appropriate measures can be taken to optimize system design and placement.
Defining System Architecture
The design of the burglar alarm system architecture is equally crucial. At this stage, choosing whether the system will be wired or wireless plays a significant role in installation dynamics.
- Wired Systems: Offer reliability and reduced risk of interference, requiring careful planning of cable routing throughout the site.
- Wireless Systems: Provide enhanced flexibility but necessitate thoughtful positioning of sensors and receivers to mitigate signal loss.
Each option has its pros and cons, contingent upon the specific requirements established during site analysis.
Developing a Layout Plan
A comprehensive layout plan should be drafted to incorporate sensor placements, alarm control panels, and keypads.
- Placement Guidelines: Sensors should be positioned to maximize coverage while minimizing false alarms—particularly around windows and doors.
- Access Points: Ensure the control panel is accessible yet protected from tampering.
Diagrams detailing these elements can be invaluable in translating the theoretical plan into a practical installation guide.
Preparing for Installation
Prior to installation, ensure all components are procured and verified against design specifications. Conduct a final review of installation guidelines, including:
- Tools Needed: Confirm that necessary tools (screwdrivers, drills, etc.) are available.
- Component Checks: Inspect all devices for functionality to avoid complications during installation.
This preemptive check can significantly enhance efficiency during the installation process.
Testing and Validation
Once installation is completed, a battery of tests must be conducted to ensure the entire system is functional. Testing should include:
- Sensor Activation: Verify that all sensors respond to stimuli as per design specifications.
- Alarm Signal: Ensure that the alarm signals reach their intended communication point and elicits appropriate responses.
Post-installation validation is essential in confirming that the system is not only operational but also resilient against potential threats.
In conclusion, the planning and installation of burglar alarm circuits involve a careful analysis of both the site and system requirements. By meticulously defining these parameters and laying out a structured approach, security systems can be optimized for both reliability and functionality.
6.2 Regular Maintenance and Testing Procedures
In the realm of security systems, the integrity of burglar alarm circuits relies heavily on consistent maintenance and testing practices. Effective monitoring not only enhances the reliability of these systems but also prolongs their operational lifespan. This section delves into the critical aspects of maintaining burglar alarm circuits and outlines comprehensive testing procedures that ensure optimal performance.
Importance of Regular Maintenance
Regular maintenance of burglar alarm circuits serves multiple purposes:
- Prevention of False Alarms: Regular checks can identify faulty sensors or wiring that might lead to unwarranted alerts.
- System Integrity: Ensures all components function as intended, thereby improving reliability and safety.
- Long-Term Cost Efficiency: Structured maintenance reduces the likelihood of costly repairs or replacements due to neglect.
Historically, neglecting such systems has resulted in failures that allowed unauthorized access to properties, underlining the critical nature of proactive measures.
Maintenance Schedule
Creating a maintenance schedule is essential for ensuring consistent oversight. A recommended schedule could include:
- Monthly Checks: Verify sensor alignment and battery levels in wireless systems.
- Quarterly Inspections: Conduct functional tests on all hardware, including sirens and control panels.
- Annual Comprehensive Review: Professionals should evaluate the entire system's layout and compatibility with current technological standards.
Testing Procedures
The systematic testing of burglar alarm circuits encompasses multiple methodologies:
Component Testing
Each component must be evaluated to establish functionality. This includes:
- Sensors: Activate each sensor individually to ensure proper response to stimuli.
- Sirens and Alarms: Test alarms to ensure they engage and emit sound at the correct levels.
- Control Panel: Verify the user interface for errors and ensure it sends signals accurately.
Response Verification
It's vital to simulate alarm events and verify the response protocols:
- Monitoring Center Check: Confirm that any alerts are received and responded to appropriately.
- User Notification: Ensure that user notifications (calls, texts, etc.) are correctly functioning.
Environmental Testing
Environmental factors can severely impact system performance. Consider testing under varying conditions:
- Simulate extreme temperatures to evaluate component resilience.
- Assess performance in different lighting conditions to validate sensor efficiency.
Documentation and Record Keeping
Maintaining accurate records of inspections, repairs, and tests helps in identifying patterns and preemptively addressing potential issues. These documents can provide valuable insight into the system's historical performance and can be crucial during upgrades.
In conclusion, incorporating a routine for regular maintenance and thorough testing of burglar alarm circuits is not merely a recommended practice, but a necessity for ensuring security systems are operationally sound and effective. Adopting these practices can significantly contribute to lowering security risks and enhancing the reliability of alarm systems.
6.3 Upgrading Alarm Systems
As technology progresses, the necessity for upgrading burglar alarm systems becomes paramount in addressing increasingly sophisticated threats. Traditional alarm systems typically offer basic functionality, primarily designed to detect unauthorized entry. However, with the advent of smart technology, integrating advanced features into burglar alarm circuits not only enhances security but also improves user experience and operational efficiency.
Modernizing the Alarm Infrastructure
Modern burglar alarm circuits can leverage new technologies, such as IoT (Internet of Things), to provide real-time monitoring and control. The integration of smart sensors, such as motion detectors with machine learning capabilities, allows for improved detection rates and reduced false alarms. Additionally, incorporating smartphone alerts and remote access enables users to monitor their properties from anywhere in the world.
Implementing Smart Sensors
To upgrade an alarm system, consider replacing conventional sensors with smart sensors. For example, a PIR (Passive Infrared) sensor combined with a microcontroller can analyze patterns in movement. These sensors can be programmed to differentiate between human presence and pets, thereby significantly decreasing false alarms.
A schematic of a potential smart sensor circuit is necessitated here:
Enhancing Communication Protocols
As alarm systems evolve, upgrading communication protocols is equally crucial. Older systems often utilized wired connections, which can be vulnerable to tampering. Implementing wireless communication through protocols such as Zigbee, Z-Wave, or Wi-Fi ensures that the systems remain functional even if the physical connections are compromised.
For instance, using a wireless transceiver can significantly simplify installation, eliminating the need for extensive cabling while enhancing the system's resiliency against physical disruptions.
Data Encryption and Security
Moreover, incorporating data encryption protocols is essential for securing communication between the alarm system and the monitoring center. Using standard encryption algorithms such as AES (Advanced Encryption Standard) can prevent unauthorized access, ensuring that even if data packets are intercepted, they cannot be decoded by malicious actors.
Integrating Additional Security Features
Beyond communication and sensor upgrades, alarm systems can be enhanced by integrating additional security features. For instance, video surveillance can be coupled with alarm systems for complete monitoring. Utilizing cameras that interface with smartphones allows users to view live footage and receive alerts on suspicious activities in real-time.
Furthermore, automated lighting systems connected to the alarm network can deter intruders by simulating occupancy, providing an additional layer of security.
Case Studies and Practical Implementations
Numerous case studies demonstrate the effectiveness of upgraded burglar alarm systems. For example, a residential complex that integrated smart security features experienced a 30% reduction in break-ins within the first year of implementation. This success is attributed to the combined technology of intelligent sensors, enhanced communication, and integrated surveillance.
Other commercial applications have shown a growing trend toward establishing centrally monitored systems that can instantly alert authorities while providing live feedback, thus optimizing response times and increasing overall safety.
In summary, upgrading burglar alarm systems involves not only the adoption of advanced sensors and communication protocols but also the thoughtful integration of additional features that enhance operational efficacy and user experience. The dynamic nature of security systems necessitates continuous innovation to combat evolving threats effectively.
In the next section, we will explore specific case studies that illustrate successful upgrades implemented by various organizations and their resultant impacts on security and resilience.
7. Key Reference Texts
7.1 Key Reference Texts
- Burglar Alarm Systems Overview - Electronics Tutorials — This tutorial provides a comprehensive overview of burglar alarm systems, including various configurations and components such as sensors and control units.
- Burglar Alarms and the Electronics Behind Them — This book delves into the electronics that power burglar alarm systems, examining sensor technologies, control circuits, and system integration.
- How to Design a Simple Burglar Alarm System - All About Circuits — A step-by-step guide on designing a basic burglar alarm system. It covers essential elements and configuration tips for reliable operation.
- Advancements in Burglar Alarm Systems Technology — This book discusses technological advancements in burglar alarm systems, including wireless technologies, IoT integration, and smart home compatibility.
- Historical Development of Burglar Alarms — An academic paper exploring the historical evolution of burglar alarms, tracing the technological and social implications of these security systems.
- Security/Fire-Alarm Systems Handbook - Elsevier — Provides a detailed guide on the design and operation of security and fire-alarm systems, which share fundamental circuits and principles with burglar alarms.
- Integrated Security Systems: Beyond Traditional Alarms — This IEEE article explores the integration of burglar alarms with advanced security systems, including network and software-enabled security solutions.
7.2 Online Resources and Tutorials
For those deeply interested in enhancing their expertise on burglar alarm circuits, a number of high-quality online resources and tutorials are available. These resources provide both theoretical insights and practical design tips, ensuring a comprehensive understanding of this critical area in electronics and security systems.
- Burglar Alarm Projects on Instructables — Instructables offers a rich repository of user-created projects detailing various types of burglar alarm circuits. Discover practical designs using simple electronic components, guided by step-by-step instructions and community feedback.
- All About Circuits Technical Articles on Security Systems — Explore technical articles on burglar alarm systems, understanding their operation, and integration with home automation. A valuable resource for theoretical insight paired with practical applications.
- Simple Junction Style Burglar Alarm — A detailed guide that breaks down the construction of a simple junction-style burglar alarm. Learn how to assemble a basic circuit that effectively detects intrusions.
- How Burglar Alarms Work - Circuit Digest — This article provides a comprehensive overview of how burglar alarms operate, discussing various sensors, alarm circuit designs, and their applications in security systems.
- Infrared Proximity Sensor Hookup Guide — An excellent tutorial on integrating infrared proximity sensors into burglar alarm circuits. Understand sensor configurations, connections, and code examples to improve detection capabilities.
- Electronics For You Magazine Tutorials — A specialized magazine with articles and DIY projects on burglar alarms. Updated regularly, it offers deep dives into specific technologies used in modern security systems.
- MIT OpenCourseWare - Electronics Tutorials — Gain access to high-quality video lectures from MIT on electronics and circuit design, including sections on building security systems like burglar alarms. A crucial resource for self-learners.
7.3 Industry Standards and Regulations
In the field of burglar alarm circuits, adhering to industry standards and regulations is essential for ensuring safety, reliability, and compatibility. This subsection explores the critical standards that govern the design and implementation of alarm systems, highlighting their significance and practical applications in real-world scenarios.
Understanding Industry Standards
Standards are established by organizations such as IEEE, IEC, and UL, which provide guidelines that influence various aspects of alarm system design, including performance, interoperability, and electromagnetic compatibility (EMC). Compliance with these standards not only helps in creating reliable systems but also ensures that they meet international safety requirements.
Key Organizations and Standards
- International Electrotechnical Commission (IEC) – The IEC 62642 series specifies requirements for alarm systems used for intruder alarms and hold-up alarms. This series addresses design principles and maintains interoperability standards, which are crucial for global product integration and deployment.
- IEEE Standards – The IEEE 802.15.4 standard is widely used for wireless communication in alarm systems, particularly in environments where cabling is impractical. It enables short-range, low-rate wireless personal area networks (WPANs).
- Underwriters Laboratories (UL) – UL 1023 covers burglar alarms for residential installations, addressing critical safety aspects and ensuring operational effectiveness to protect occupants and property.
Practical Relevance and Application
Adherence to these standards ensures that burglar alarm circuits perform efficiently under various conditions. Systems designed according to these standards benefit from increased reliability and are more likely to gain consumer trust. Moreover, industry compliance is a prerequisite for insurance eligibility in many jurisdictions.
Mathematical Foundations in Standards Compliance
To quantify the performance requirements, some mathematical models are employed to analyze signal integrity and power management aspects. For example, the load factor in a circuit can be represented mathematically for reliability assessments.
The above equation describes the power demand of a component within an alarm circuit, where V is the voltage and Iload is the load current. Standards ensure that systems handle defined power levels without degradation in performance.
Historical Context and Development
Historically, standards for burglar alarm systems emerged as the technology evolved from simple mechanical alarms to sophisticated electronic networks. Early adopters like banks and government facilities drove demand for reliable systems, leading to the establishment of formal guidelines and widespread adoption.
Innovation continues to drive the evolution of these standards, ensuring they remain relevant in the face of new threats, technologies, and user demands globally.