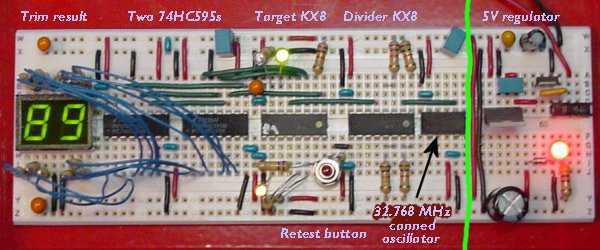
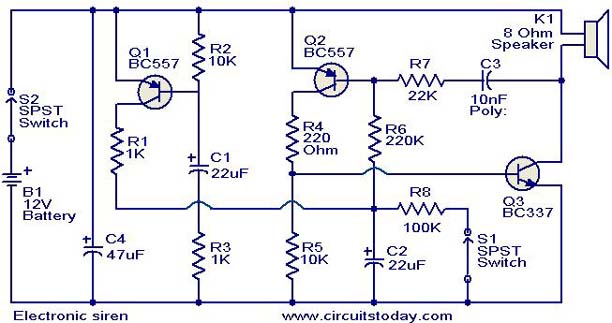
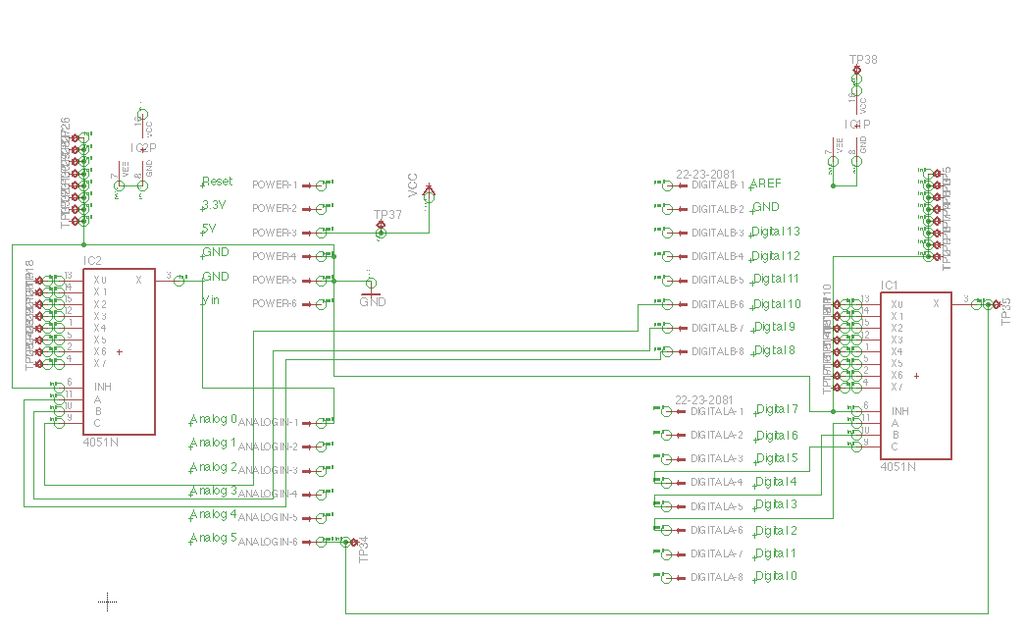
electronic hotel door vulnerability using stealth lock circuit

The term "pentester" refers to a penetration tester, individuals who assess security vulnerabilities. Many high-end hotels globally depend on keycard locks for securing hotel rooms. However, recent incidents of theft have shown that these locks may not be as secure as previously thought, as evidenced by a series of thefts linked to hacking these locks.
Keycard locks are electronic locking mechanisms that utilize a card with a magnetic stripe or RFID (Radio Frequency Identification) technology to grant access to hotel rooms. These systems are designed to enhance security and convenience for guests. However, vulnerabilities in the electronic systems can be exploited by skilled individuals, leading to unauthorized access.
The hacking of keycard locks typically involves exploiting weaknesses in the communication protocols or the encryption methods used in the locking mechanisms. Attackers may use specialized equipment to clone keycards or manipulate the locking system, bypassing the security measures intended to protect guests' belongings.
To mitigate these risks, hotels can adopt several strategies. Implementing stronger encryption methods, regularly updating firmware, and conducting penetration tests can help identify and address vulnerabilities. Additionally, using two-factor authentication systems can add an extra layer of security, ensuring that even if a keycard is compromised, unauthorized access can still be prevented.
Overall, while keycard locks provide a level of convenience and security, continuous evaluation and enhancement of their security measures are essential to protect against evolving threats in the realm of electronic security.The word "pentester" actually stands for penetration tester, people who tests security vulnerabi. Most of the high-end hotels around the world rely on keycard locks for the security of hotel rooms. However, these locks may not be so secure after all as a fresh string of thefts that have been perpetuated by `hacking` these locks has demonstrated. 🔗 External reference
Keycard locks are electronic locking mechanisms that utilize a card with a magnetic stripe or RFID (Radio Frequency Identification) technology to grant access to hotel rooms. These systems are designed to enhance security and convenience for guests. However, vulnerabilities in the electronic systems can be exploited by skilled individuals, leading to unauthorized access.
The hacking of keycard locks typically involves exploiting weaknesses in the communication protocols or the encryption methods used in the locking mechanisms. Attackers may use specialized equipment to clone keycards or manipulate the locking system, bypassing the security measures intended to protect guests' belongings.
To mitigate these risks, hotels can adopt several strategies. Implementing stronger encryption methods, regularly updating firmware, and conducting penetration tests can help identify and address vulnerabilities. Additionally, using two-factor authentication systems can add an extra layer of security, ensuring that even if a keycard is compromised, unauthorized access can still be prevented.
Overall, while keycard locks provide a level of convenience and security, continuous evaluation and enhancement of their security measures are essential to protect against evolving threats in the realm of electronic security.The word "pentester" actually stands for penetration tester, people who tests security vulnerabi. Most of the high-end hotels around the world rely on keycard locks for the security of hotel rooms. However, these locks may not be so secure after all as a fresh string of thefts that have been perpetuated by `hacking` these locks has demonstrated. 🔗 External reference