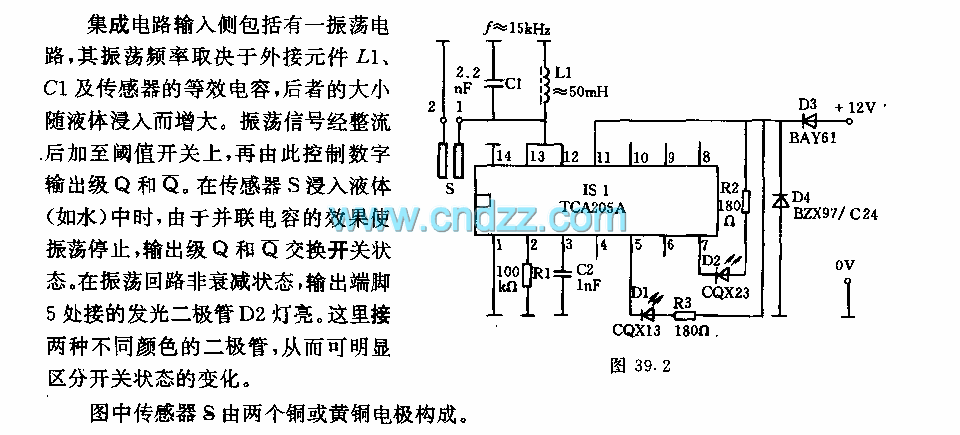
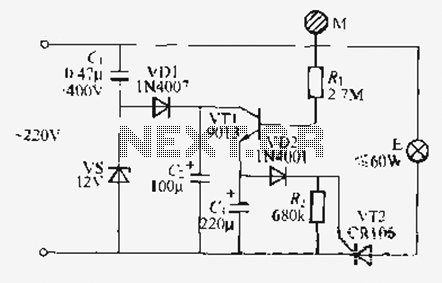
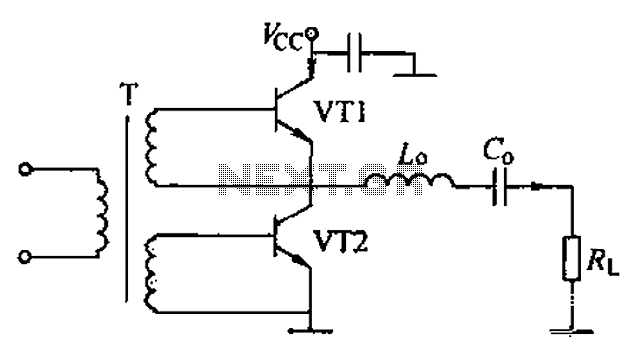
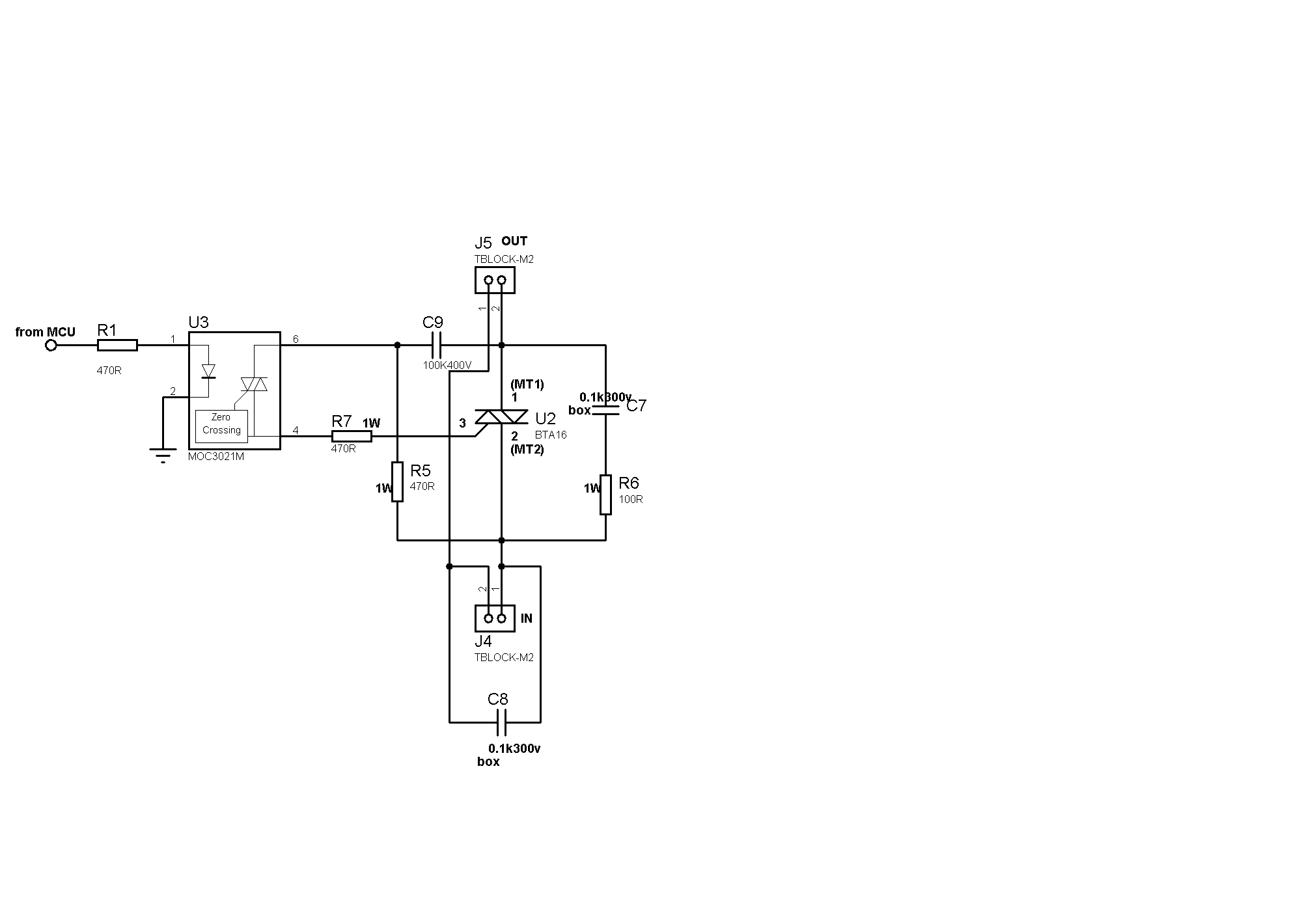
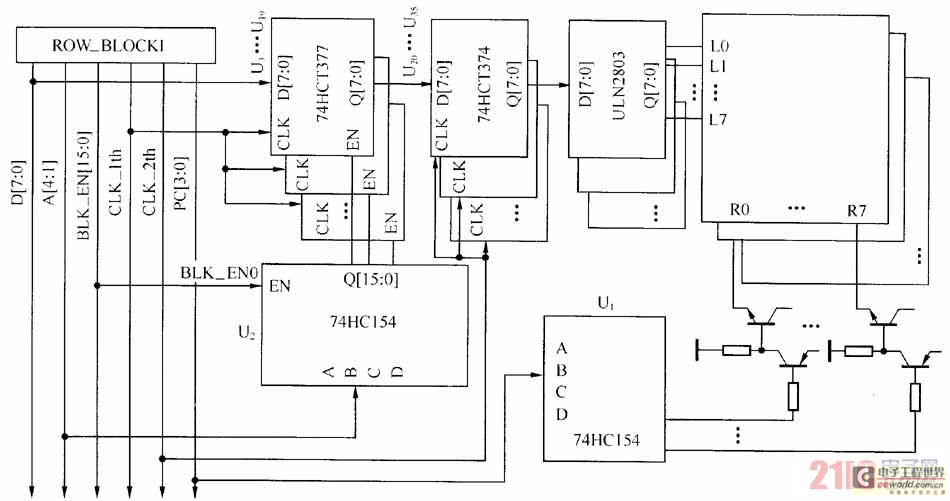
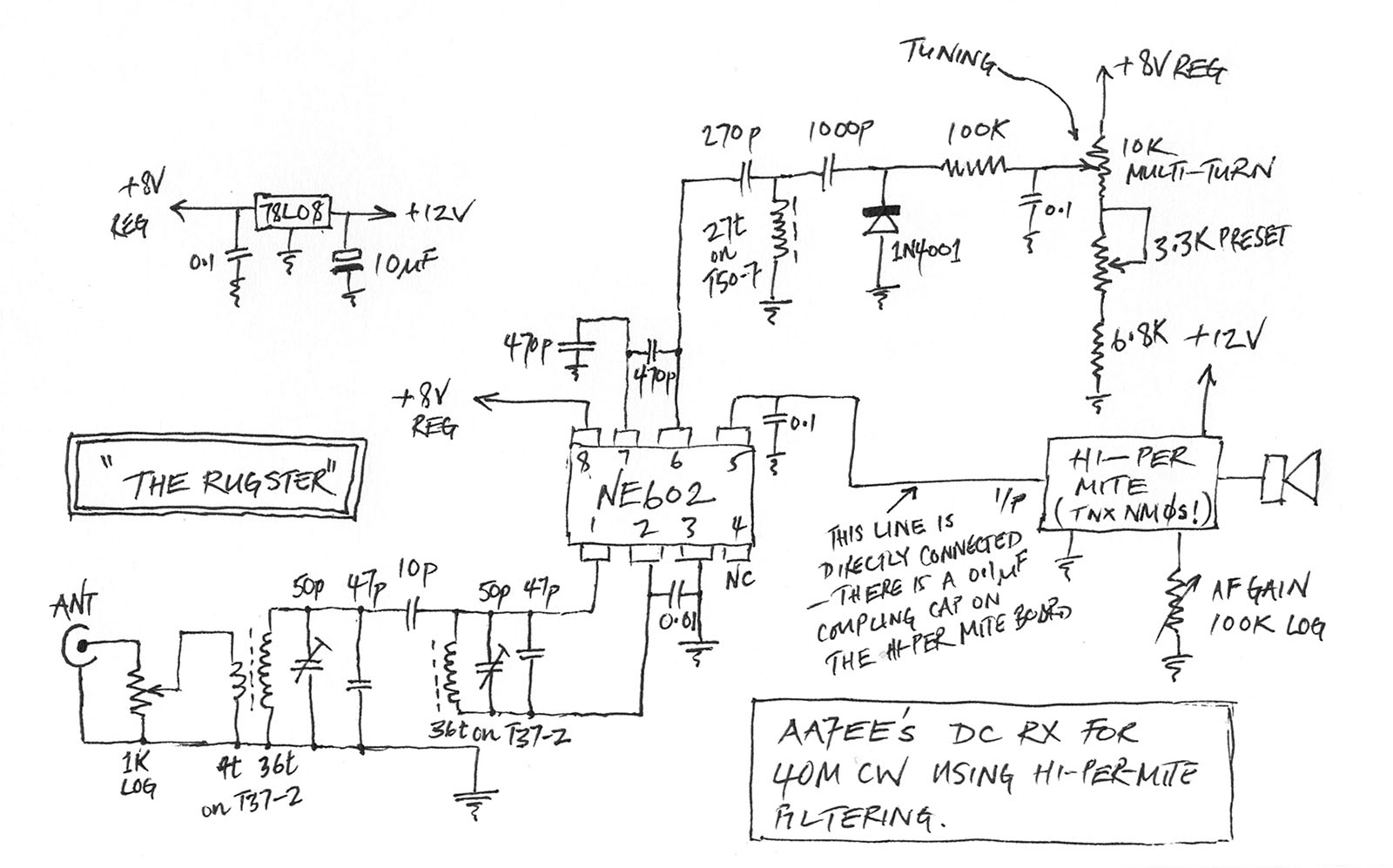
Hard Disk Switch

In today's environment, characterized by viruses and various threats from the Internet, it is essential to have assurance that a PC remains protected from infections. This circuit...
To enhance the security of personal computers against viral threats and malware, a comprehensive circuit design can be implemented. This design may include several key components such as a microcontroller, intrusion detection sensors, and a network monitoring module.
The core of the circuit can be a microcontroller unit (MCU) that acts as the central processing unit. The MCU can be programmed to monitor system activities and detect any anomalies that may indicate a virus or malware infection. It can be interfaced with various sensors that monitor network traffic, file integrity, and system performance metrics.
An intrusion detection system (IDS) can be integrated into the circuit, utilizing both signature-based and anomaly-based detection methods. Signature-based detection involves comparing incoming data against a database of known threats, while anomaly-based detection establishes a baseline of normal behavior and flags deviations from this norm.
To further enhance the security measures, a network monitoring module can be included to analyze traffic patterns and identify suspicious activities. This module can utilize techniques such as packet sniffing and flow analysis to detect potential threats in real-time. The findings can be relayed back to the MCU for processing and action.
Additionally, the circuit can incorporate a user interface, allowing users to receive alerts and notifications regarding potential threats. This interface can be designed using LEDs or a small display screen, providing a visual representation of the system's status.
Power supply considerations are also crucial in this design. A stable power source, such as a regulated power supply or battery backup, should be implemented to ensure continuous operation of the circuit, even during power outages.
Overall, this circuit design emphasizes the importance of proactive measures in safeguarding personal computers from the myriad of threats present in today's digital landscape.In these times with viruses and other threats from the Internet it would be nice to have reassurance that the PC cannot be infected. That is why this circ.. 🔗 External reference
To enhance the security of personal computers against viral threats and malware, a comprehensive circuit design can be implemented. This design may include several key components such as a microcontroller, intrusion detection sensors, and a network monitoring module.
The core of the circuit can be a microcontroller unit (MCU) that acts as the central processing unit. The MCU can be programmed to monitor system activities and detect any anomalies that may indicate a virus or malware infection. It can be interfaced with various sensors that monitor network traffic, file integrity, and system performance metrics.
An intrusion detection system (IDS) can be integrated into the circuit, utilizing both signature-based and anomaly-based detection methods. Signature-based detection involves comparing incoming data against a database of known threats, while anomaly-based detection establishes a baseline of normal behavior and flags deviations from this norm.
To further enhance the security measures, a network monitoring module can be included to analyze traffic patterns and identify suspicious activities. This module can utilize techniques such as packet sniffing and flow analysis to detect potential threats in real-time. The findings can be relayed back to the MCU for processing and action.
Additionally, the circuit can incorporate a user interface, allowing users to receive alerts and notifications regarding potential threats. This interface can be designed using LEDs or a small display screen, providing a visual representation of the system's status.
Power supply considerations are also crucial in this design. A stable power source, such as a regulated power supply or battery backup, should be implemented to ensure continuous operation of the circuit, even during power outages.
Overall, this circuit design emphasizes the importance of proactive measures in safeguarding personal computers from the myriad of threats present in today's digital landscape.In these times with viruses and other threats from the Internet it would be nice to have reassurance that the PC cannot be infected. That is why this circ.. 🔗 External reference