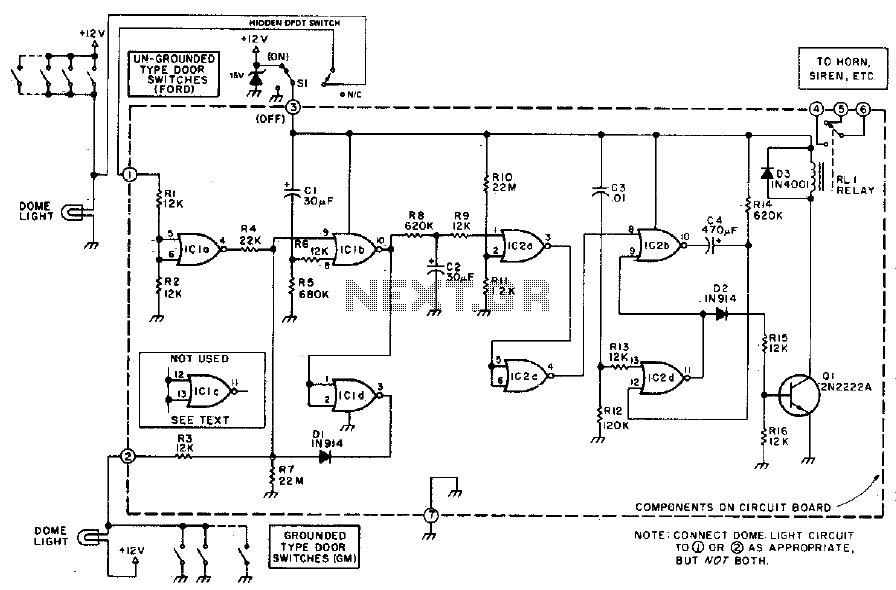
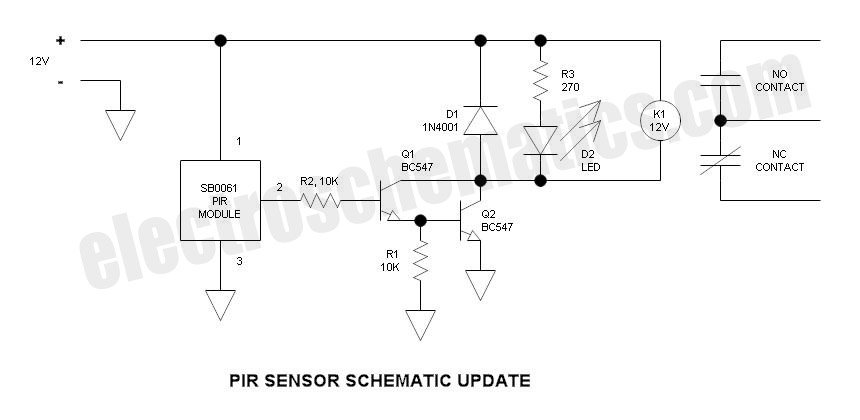
RFID Based Security System with AT89S52

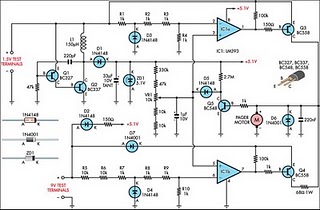
This project aimed to develop a wireless system to detect and allow only the authorized persons. The system was based on Radio Frequency Identification (RFID) technology and consists of a passive RFID tag. The passive micro transponder tag collects power from the 125 KHz magnetic field generated by the base station, gathers information about the Tag ID and sends this information to the base station. More: The base station receives, decodes and checks the information available in its Database and Manchester code was used to send those information. The system performed as desired with a 10cm diameter antenna attached to the transponder. The Base Station is b
The described project implements a wireless access control system utilizing Radio Frequency Identification (RFID) technology, specifically employing passive RFID tags. The core component of the system is the passive micro transponder tag, which operates by harvesting energy from the electromagnetic field produced by the base station. The operational frequency of 125 kHz is standard for many RFID applications, allowing for effective communication over short distances.
The passive RFID tag is designed to respond to the magnetic field generated by the base station. When within range, the tag absorbs energy from this field, enabling it to power its internal circuitry. This energy harvesting process allows the tag to transmit its unique Tag ID back to the base station. The communication protocol utilized is based on Manchester coding, which provides a reliable method for encoding the data to ensure proper synchronization and error detection during transmission.
The base station is equipped to receive the signals from the RFID tags, decode the transmitted Tag ID, and compare it against a pre-existing database of authorized users. This database may be stored in non-volatile memory, allowing for persistent access control even during power outages. Upon successful identification of an authorized Tag ID, the base station can trigger an output mechanism, such as unlocking a door or granting access to a restricted area.
The system's performance has been validated with a 10 cm diameter antenna attached to the transponder, which enhances the effective range and reliability of the communication between the tag and the base station. The overall design is compact and efficient, making it suitable for various applications in security and access control environments. The implementation of this RFID-based system presents a robust solution for ensuring that only authorized individuals gain access to designated areas or information.This project aimed to develop a wireless system to detect and allow only the authorized persons. The system was based on Radio Frequency Identification (RFID) technology and consists of a passive RFID tag. The passive micro transponder tag collects power from the 125 KHz magnetic field generated by the base station, gathers information about the Tag ID and sends this information to the base station.
The base station receives, decodes and checks the information available in its Database and Manchester code was used to send those information. The system performed as desired with a 10cm diameter antenna attached to the transponder. The Base Station is b 🔗 External reference
The described project implements a wireless access control system utilizing Radio Frequency Identification (RFID) technology, specifically employing passive RFID tags. The core component of the system is the passive micro transponder tag, which operates by harvesting energy from the electromagnetic field produced by the base station. The operational frequency of 125 kHz is standard for many RFID applications, allowing for effective communication over short distances.
The passive RFID tag is designed to respond to the magnetic field generated by the base station. When within range, the tag absorbs energy from this field, enabling it to power its internal circuitry. This energy harvesting process allows the tag to transmit its unique Tag ID back to the base station. The communication protocol utilized is based on Manchester coding, which provides a reliable method for encoding the data to ensure proper synchronization and error detection during transmission.
The base station is equipped to receive the signals from the RFID tags, decode the transmitted Tag ID, and compare it against a pre-existing database of authorized users. This database may be stored in non-volatile memory, allowing for persistent access control even during power outages. Upon successful identification of an authorized Tag ID, the base station can trigger an output mechanism, such as unlocking a door or granting access to a restricted area.
The system's performance has been validated with a 10 cm diameter antenna attached to the transponder, which enhances the effective range and reliability of the communication between the tag and the base station. The overall design is compact and efficient, making it suitable for various applications in security and access control environments. The implementation of this RFID-based system presents a robust solution for ensuring that only authorized individuals gain access to designated areas or information.This project aimed to develop a wireless system to detect and allow only the authorized persons. The system was based on Radio Frequency Identification (RFID) technology and consists of a passive RFID tag. The passive micro transponder tag collects power from the 125 KHz magnetic field generated by the base station, gathers information about the Tag ID and sends this information to the base station.
The base station receives, decodes and checks the information available in its Database and Manchester code was used to send those information. The system performed as desired with a 10cm diameter antenna attached to the transponder. The Base Station is b 🔗 External reference