Motorcycle anti-theft lock electronic circuit
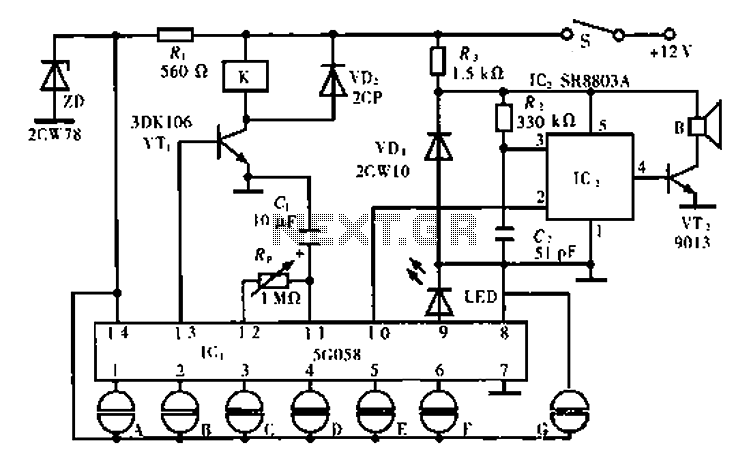
The circuit operates using an ASIC lock IC, specifically the 5C058. Pins 1 to 6 are connected outside the key switch to the positive power supply, representing six valid key inputs. To unlock, keys A through F must be pressed in the correct sequence. Pin 7 serves as the negative power connection, while pin 8 is designated for the false key input terminal, which can also be connected outside the invalid key switch. The design allows for the possibility of mixing one or several keys on the keyboard to avoid false signals.
The 5C058 ASIC lock circuit is designed for secure access control applications. It utilizes a sequence of valid key inputs to unlock, ensuring that only authorized users can gain access. The valid key inputs are connected to pins 1 through 6, which are linked to a key switch mechanism. When the correct sequence of keys A through F is pressed, the circuit recognizes the input and activates the unlocking mechanism.
The negative power supply is connected to pin 7, which ensures that the circuit has a common ground reference, essential for stable operation. The false key input terminal at pin 8 is a critical feature that enhances the security of the lock. This terminal can be connected to an invalid key switch, allowing the circuit to identify and disregard spurious inputs that do not conform to the valid key sequence.
The circuit's ability to accept mixed inputs is a unique feature that provides flexibility in operation. Users can press multiple keys simultaneously or in quick succession without triggering a false unlock response. This design consideration is important in environments where security is paramount, as it prevents unauthorized access through accidental or unintentional key presses.
Overall, the 5C058 ASIC lock circuit represents a robust solution for electronic locking mechanisms, combining ease of use with advanced security features to protect sensitive areas or devices.Circuit works: lC1 is lock ASIC 5C058. Its 1-6 feet were even outside the key switch to the positive power supply, which is six valid key input, open lock A-F must comply with this order. 7 feet for the negative power. 8 feet false key input terminal, even outside an invalid key switch. You can take one or several mixed into the keyboard in order to leave spurious.
The 5C058 ASIC lock circuit is designed for secure access control applications. It utilizes a sequence of valid key inputs to unlock, ensuring that only authorized users can gain access. The valid key inputs are connected to pins 1 through 6, which are linked to a key switch mechanism. When the correct sequence of keys A through F is pressed, the circuit recognizes the input and activates the unlocking mechanism.
The negative power supply is connected to pin 7, which ensures that the circuit has a common ground reference, essential for stable operation. The false key input terminal at pin 8 is a critical feature that enhances the security of the lock. This terminal can be connected to an invalid key switch, allowing the circuit to identify and disregard spurious inputs that do not conform to the valid key sequence.
The circuit's ability to accept mixed inputs is a unique feature that provides flexibility in operation. Users can press multiple keys simultaneously or in quick succession without triggering a false unlock response. This design consideration is important in environments where security is paramount, as it prevents unauthorized access through accidental or unintentional key presses.
Overall, the 5C058 ASIC lock circuit represents a robust solution for electronic locking mechanisms, combining ease of use with advanced security features to protect sensitive areas or devices.Circuit works: lC1 is lock ASIC 5C058. Its 1-6 feet were even outside the key switch to the positive power supply, which is six valid key input, open lock A-F must comply with this order. 7 feet for the negative power. 8 feet false key input terminal, even outside an invalid key switch. You can take one or several mixed into the keyboard in order to leave spurious.