Networking Security System (ATmega16L)
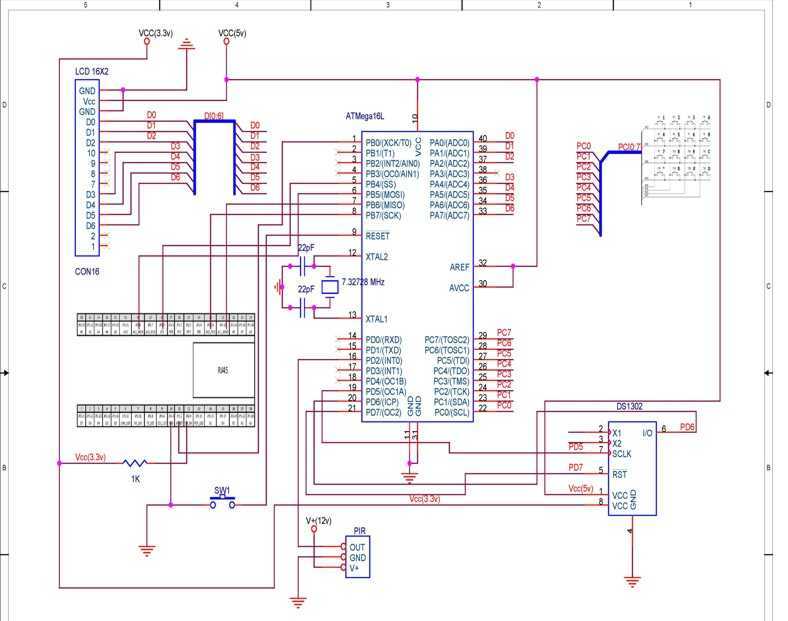
TCP based security system using the Ethernet module offered within the contest, an ATmega16L microcontroller, a PIR as a sensor and few other peripheral devices, which is specially targeted for homes and small business owners. I have used through for my final design a combination of the WIZ810MJ module, an ATmega16L microcontroller, a 7.3728 MHz crystal (compatible with my bootloader programmer), a DS1302 timekeeper, a PIR to sense the human movement through the body heat, a keypad for initial configuration and a 2×16 LCD for display. The design also include regulators to power up the circuits. More: Well, the system should be installed near an internet source and a cable (crossover or straight-through as it depends) should be plugged in to the module's RJ-45 jack.
If the system is in rest mode (acting as TCP server). It waits for commands from the client (its IP address can be programmed or changed initially or during operation) and execute them (after a password is entered obviously) while still inspecting for any Alarm which would arise from the PIR sensor. When any Alarm triggers, it switches into client mode (acts as a TCP client) and starts sending warning signs.
The system uses motion sensing (based on human body heat) to trigger an alarm which sends a message to the server containing a timestamp presenting the exact time the Motion was detected acting as a real-time surveillance system. For increasing safety from the risk arising from a false alarm, it sends the alarm signals for about 5 minutes and then it stops for 10 minutes and so on assuming the alarm was still active... Clearing the way for the customer to stop the alarm if he noticed some kind of a failure as the system acts as a server in these 10 minutes. This false alarm is very rare and it could occur as a result of maybe a passing squirrel or some relative passed by and forgot to turn the alarm off... etc. So although it is rare but should be taken care of. In the first start-up of the system, it enters the configuration mode. It is just a feature that I added for the design to be more flexible. The System asks you first (through the LCD interface) to enter a 4 digit password, I didn’t do a masking feature because I sense there would be less error when you can really see the password written on the LCD, and there isn’t off course any viruses or key loggers are there?!
The system will also ask you about the current date and time which is necessary for the validity of the timestamp associated with the Alarms. Otherwise, if the time was mis-entered, the customer may lose track of when the alarm was really triggered.
After entering the current date the system asks the customer to choose between accepting the default IP setting or reconfigure them depending on his own needs. The customer will be asked to enter the System IP Address, the subnet mask, the default gateway address, the MAC address desired, and the destination or Server IP address in which will give commands remotely to the security system and will also receive Alarm signals when the motion is sensed. and here ends the configuration, I didn’t really see any more necessary feature to add to the configuration, but this doesn’t block the way for future improvement as minor adjustments could be made and the user could be given more flexibility in the future versions. Once it is connected and powered on, (it takes power from 3 sources, 3.3v, 5v, and 12v for the PIR) the system enters into the configuration mode.
The described TCP-based security system integrates several key components to ensure effective monitoring and control. The ATmega16L microcontroller serves as the central processing unit, managing the interactions between the various peripherals. The WIZ810MJ Ethernet module facilitates network connectivity, allowing the system to communicate with a remote server over TCP/IP.
The PIR sensor is crucial for detecting human movement through infrared sensing, triggering alarms based on changes in body heat. The system's operational modes include a server mode for awaiting commands and a client mode for alerting the server upon detecting movement. The configuration interface is user-friendly, utilizing a 2×16 LCD display and a keypad for input, making the system accessible for initial setup and adjustments.
The power supply design incorporates voltage regulators to accommodate the different voltage requirements of the system components, ensuring stable operation. The DS1302 real-time clock module is essential for maintaining accurate timestamps, which are critical for logging alarm events.
The alarm signaling mechanism is designed to mitigate false alarms by implementing a timed response strategy, where alerts are sent for a duration of five minutes followed by a ten-minute cooldown period. This approach allows users to verify the validity of an alarm without overwhelming them with notifications.
Overall, the system is tailored for ease of use and flexibility, with provisions for future enhancements to expand its functionality. The configuration process allows users to set their security preferences, including IP settings and alarm parameters, ensuring the system can adapt to different environments and user needs.TCP based security system using the Ethernet module offered within the contest , an ATmega16L microcontroller , a PIR as a sensor and few other peripheral devices , which is specially targeted for homes and small business owners. I have used through for my final design a combination of the WIZ810MJ module , an ATmega16L microcontroller , a 7.3728 MHz crystal (compatible with my bootloader programmer), a DS1302 timekeeper , a PIR to sense the human movement through the body heat , a keypad for initial configuration and a 2×16 LCD for display.
The design also include regulators to power up the circuits. Well , the system should be installed near an internet source and a cable (crossover or straight-through as it depends) should be plugged in to the module?s Rj-45 jack. If the system is in rest mode (acting as TCP server) . It waits for commands from the client (its IP address can be programmed or change initially or during operation) and execute them (after a password is entered obviously )while still inspecting for any Alarm which would arises from the PIR sensor .
When any Alarm triggers , it switches into client mode (acts as a TCP client) and starts sending warning signs. The system uses motion sensing (based on human body heat) to trigger an alarm which sends a message to the server containing a timestamp presenting the exact time the Motion was detected acting as a real-time surveillance system .
For increasing safety from the risk arising from a false alarm , it sends the alarm signals for about 5 minutes and then it stops for 10 minutes and so on assuming the alarm was still active ... Clearing the way for the costumer to stop the alarm if he noticed some kind of a failure as the system acts as a server in these 10 minutes.
This false alarm is very rare and it could occur as a result of maybe a passing squirrel maybe or some relative passed by and forgot to turn the alarm off .. etc .. So although it is rare but should be taken care of. In the first start-up of the system, it enters the configuration mode . It is just a feature that I added for the design to be more flexible. The System asks you first (through the LCD interface) to enter a 4 digit password , I didn?t do a masking feature because I sense there would be less error when you can really see the password written on the LCD , and there isn?t off course any viruses or key loggers are there ?!
The system will also ask you about the current date and time which is necessary for the validity of the timestamp associated with the Alarms. Otherwise, if the time was miss-entered ,the customer may lose track of when the alarm was really triggered.
After entering the current date the system asks the customer to chose between accepting the default IP setting or reconfigure them depending on his own needs . The customer will be asked to enter the System IP Address ,the subnet mask, the default gateway address , the MAC address desired , and the destination or Server IP address in which will give commands remotely to the security system and will also receive Alarm signals when the motion is sensed .
and here ends the configuration , I didn?t really see any more necessary feature to add to the configuration ,but this doesn?t block the way for future improvement as minor adjustments could be made and the user could be given more flexibility in the future versions. Once it is connected and powered on , (it takes power from 3 sources ,3.3v ,5v,and 12 v for the PIR) the system enters into the configuration mode .
🔗 External reference
If the system is in rest mode (acting as TCP server). It waits for commands from the client (its IP address can be programmed or changed initially or during operation) and execute them (after a password is entered obviously) while still inspecting for any Alarm which would arise from the PIR sensor. When any Alarm triggers, it switches into client mode (acts as a TCP client) and starts sending warning signs.
The system uses motion sensing (based on human body heat) to trigger an alarm which sends a message to the server containing a timestamp presenting the exact time the Motion was detected acting as a real-time surveillance system. For increasing safety from the risk arising from a false alarm, it sends the alarm signals for about 5 minutes and then it stops for 10 minutes and so on assuming the alarm was still active... Clearing the way for the customer to stop the alarm if he noticed some kind of a failure as the system acts as a server in these 10 minutes. This false alarm is very rare and it could occur as a result of maybe a passing squirrel or some relative passed by and forgot to turn the alarm off... etc. So although it is rare but should be taken care of. In the first start-up of the system, it enters the configuration mode. It is just a feature that I added for the design to be more flexible. The System asks you first (through the LCD interface) to enter a 4 digit password, I didn’t do a masking feature because I sense there would be less error when you can really see the password written on the LCD, and there isn’t off course any viruses or key loggers are there?!
The system will also ask you about the current date and time which is necessary for the validity of the timestamp associated with the Alarms. Otherwise, if the time was mis-entered, the customer may lose track of when the alarm was really triggered.
After entering the current date the system asks the customer to choose between accepting the default IP setting or reconfigure them depending on his own needs. The customer will be asked to enter the System IP Address, the subnet mask, the default gateway address, the MAC address desired, and the destination or Server IP address in which will give commands remotely to the security system and will also receive Alarm signals when the motion is sensed. and here ends the configuration, I didn’t really see any more necessary feature to add to the configuration, but this doesn’t block the way for future improvement as minor adjustments could be made and the user could be given more flexibility in the future versions. Once it is connected and powered on, (it takes power from 3 sources, 3.3v, 5v, and 12v for the PIR) the system enters into the configuration mode.
The described TCP-based security system integrates several key components to ensure effective monitoring and control. The ATmega16L microcontroller serves as the central processing unit, managing the interactions between the various peripherals. The WIZ810MJ Ethernet module facilitates network connectivity, allowing the system to communicate with a remote server over TCP/IP.
The PIR sensor is crucial for detecting human movement through infrared sensing, triggering alarms based on changes in body heat. The system's operational modes include a server mode for awaiting commands and a client mode for alerting the server upon detecting movement. The configuration interface is user-friendly, utilizing a 2×16 LCD display and a keypad for input, making the system accessible for initial setup and adjustments.
The power supply design incorporates voltage regulators to accommodate the different voltage requirements of the system components, ensuring stable operation. The DS1302 real-time clock module is essential for maintaining accurate timestamps, which are critical for logging alarm events.
The alarm signaling mechanism is designed to mitigate false alarms by implementing a timed response strategy, where alerts are sent for a duration of five minutes followed by a ten-minute cooldown period. This approach allows users to verify the validity of an alarm without overwhelming them with notifications.
Overall, the system is tailored for ease of use and flexibility, with provisions for future enhancements to expand its functionality. The configuration process allows users to set their security preferences, including IP settings and alarm parameters, ensuring the system can adapt to different environments and user needs.TCP based security system using the Ethernet module offered within the contest , an ATmega16L microcontroller , a PIR as a sensor and few other peripheral devices , which is specially targeted for homes and small business owners. I have used through for my final design a combination of the WIZ810MJ module , an ATmega16L microcontroller , a 7.3728 MHz crystal (compatible with my bootloader programmer), a DS1302 timekeeper , a PIR to sense the human movement through the body heat , a keypad for initial configuration and a 2×16 LCD for display.
The design also include regulators to power up the circuits. Well , the system should be installed near an internet source and a cable (crossover or straight-through as it depends) should be plugged in to the module?s Rj-45 jack. If the system is in rest mode (acting as TCP server) . It waits for commands from the client (its IP address can be programmed or change initially or during operation) and execute them (after a password is entered obviously )while still inspecting for any Alarm which would arises from the PIR sensor .
When any Alarm triggers , it switches into client mode (acts as a TCP client) and starts sending warning signs. The system uses motion sensing (based on human body heat) to trigger an alarm which sends a message to the server containing a timestamp presenting the exact time the Motion was detected acting as a real-time surveillance system .
For increasing safety from the risk arising from a false alarm , it sends the alarm signals for about 5 minutes and then it stops for 10 minutes and so on assuming the alarm was still active ... Clearing the way for the costumer to stop the alarm if he noticed some kind of a failure as the system acts as a server in these 10 minutes.
This false alarm is very rare and it could occur as a result of maybe a passing squirrel maybe or some relative passed by and forgot to turn the alarm off .. etc .. So although it is rare but should be taken care of. In the first start-up of the system, it enters the configuration mode . It is just a feature that I added for the design to be more flexible. The System asks you first (through the LCD interface) to enter a 4 digit password , I didn?t do a masking feature because I sense there would be less error when you can really see the password written on the LCD , and there isn?t off course any viruses or key loggers are there ?!
The system will also ask you about the current date and time which is necessary for the validity of the timestamp associated with the Alarms. Otherwise, if the time was miss-entered ,the customer may lose track of when the alarm was really triggered.
After entering the current date the system asks the customer to chose between accepting the default IP setting or reconfigure them depending on his own needs . The customer will be asked to enter the System IP Address ,the subnet mask, the default gateway address , the MAC address desired , and the destination or Server IP address in which will give commands remotely to the security system and will also receive Alarm signals when the motion is sensed .
and here ends the configuration , I didn?t really see any more necessary feature to add to the configuration ,but this doesn?t block the way for future improvement as minor adjustments could be made and the user could be given more flexibility in the future versions. Once it is connected and powered on , (it takes power from 3 sources ,3.3v ,5v,and 12 v for the PIR) the system enters into the configuration mode .
🔗 External reference