Bugging Countermeasure
This system enables a Technical Surveillance Countermeasures (TSCM) specialist to briefly activate a Spectronics bugging device for a second or two to identify its presence, then deactivate it before the eavesdropper realizes that their device has been detected. A limited set of 12-bit "house" activation codes can be processed in less than a second, totaling around 6-8 codes. If these basic sequences are unsuccessful, the full 12-bit sequence must be executed, which takes less than ten minutes. The signal is transmitted at 433.92 MHz as an AFSK data stream, allowing most users to easily detect the bug. The entire RF transit section powers down during sleep mode, while the receive section remains active, continuously monitoring the command channel. These bugs can be quickly located using bypass codes (less than a second) or the full sequence (under ten minutes) due to the small activation key size and known frequency. An alternative detection method involves using eight car alarm remotes (12+ bits), pressing each button in sequence. Each remote must be reprogrammed with the activation codes, but the sequence is only two bytes long. Companies like Oregon Scientific and Davis Instruments manufacture wireless digital thermometers that operate on the same frequency and bit stream as these Spectronics eavesdropping devices. However, using these thermometers during a bug sweep may accidentally trigger the eavesdropping device as environmental conditions change. Handheld code grabbers from the car alarm and garage door opener industries can effectively track these devices, although legal implications may arise from their use. To execute the complete sequence of house command signals, 128 bits of data or 16 characters are required. This is significant because a wireless keyboard operating at 433.92 MHz can also be used to input the 16-character "all on" sequence. However, using a car alarm remote is generally simpler. If searching through all 12-bit variations, a more sophisticated method capable of processing the entire sequence is necessary. Spectronics is not the sole company utilizing this frequency or the 12-bit activation code. To effectively disrupt an eavesdropper, the same sequence can be transmitted simultaneously at 310 MHz and 916 MHz along with the 433 MHz codes. The command structure consists of a four-bit command word in addition to a 12-bit addressing word. The scrambling method employed by the audio circuit eavesdropping system is basic frequency inversion, which can be monitored by many scanners or decoded on a PC. Individuals conducting a bug sweep who hear the distinct "Donald Duck" sound on their TSCM equipment recognize they are tracking a live bug and may experience heightened anxiety until the device is located. The physical dimensions of the bugging devices are 35 x 23 x 8 mm (approximately 1.5 cubic inches) for one model and 31 x 19 x 6.1 mm for another. A schematic for the receiver section of the bug reveals a notable design flaw that TSCM professionals can exploit for detection purposes.
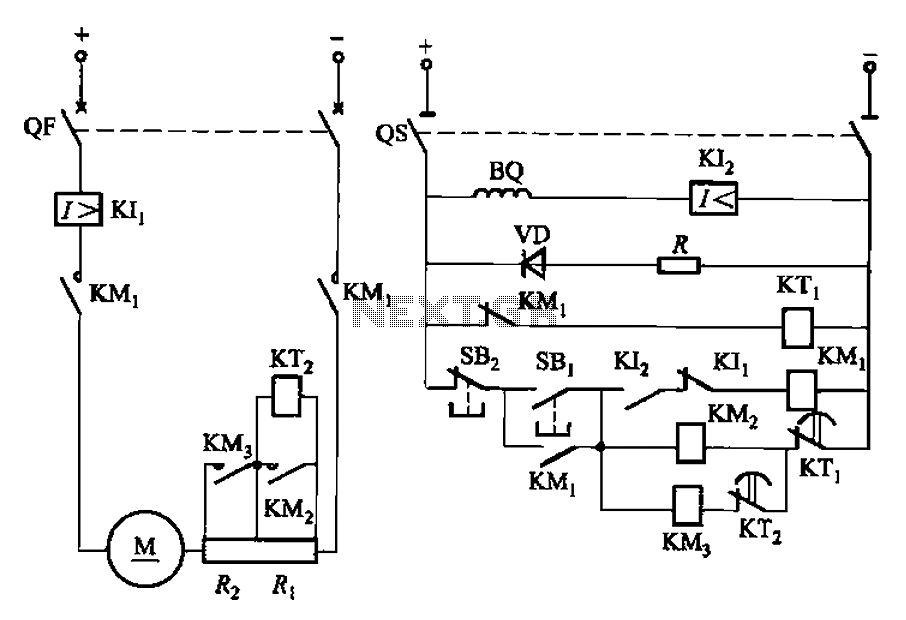
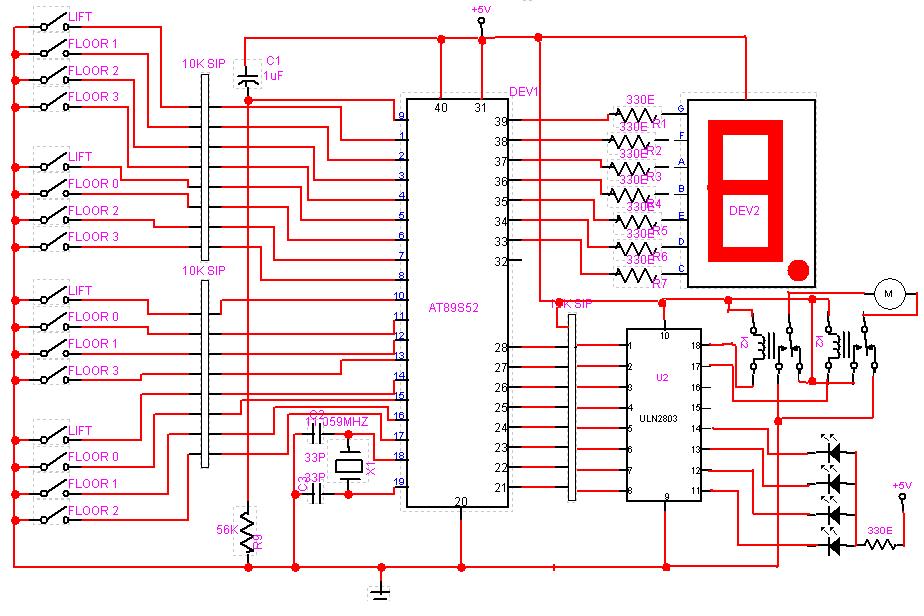
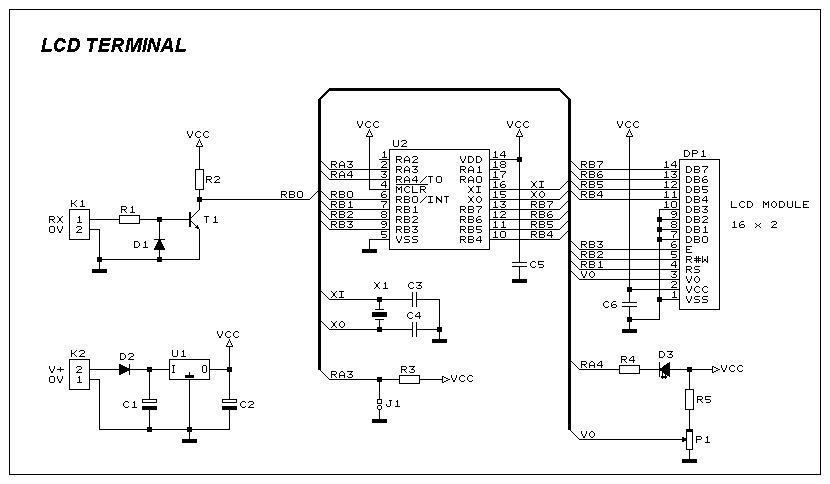
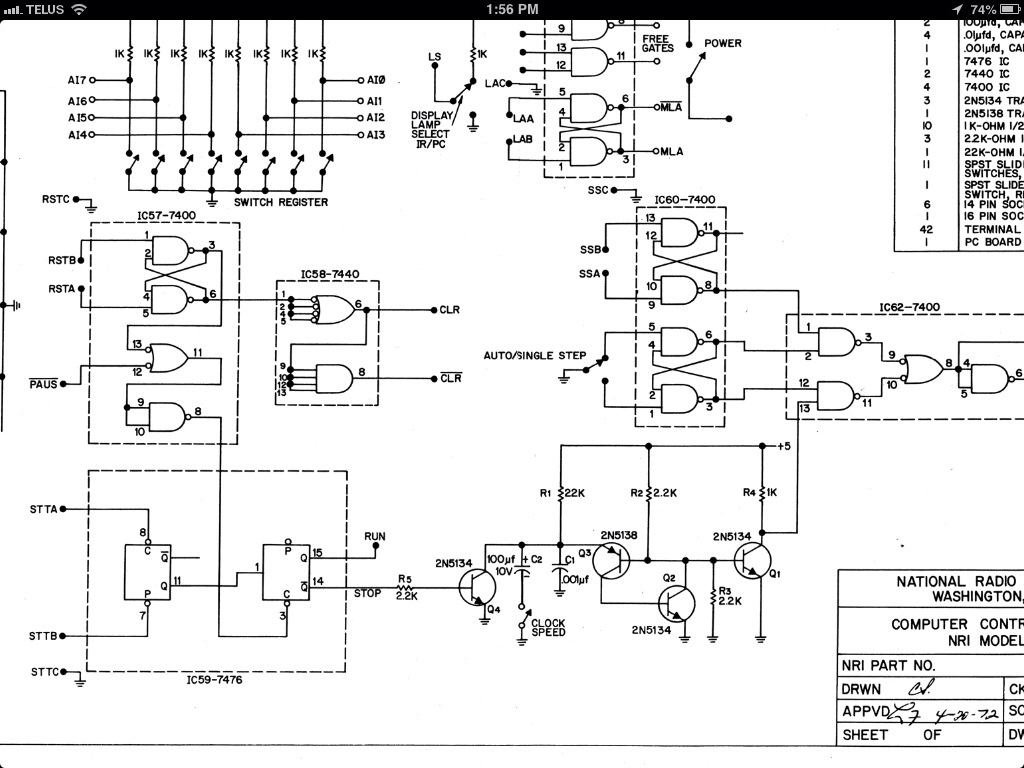
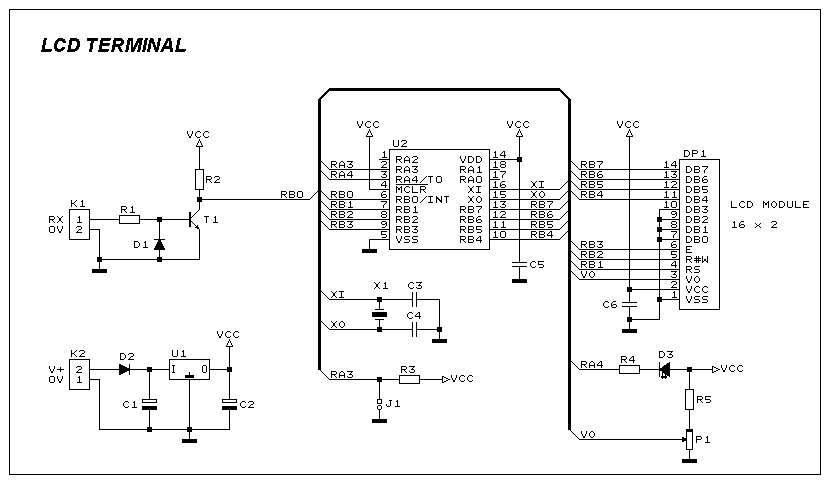
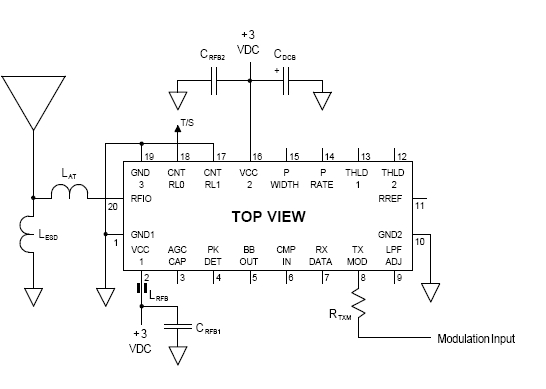
The electronic schematic for the receiver section of the Spectronics bugging device is critical for understanding its operation and vulnerabilities. The receiver is typically designed to operate within the 433.92 MHz frequency band, utilizing a superheterodyne architecture to demodulate the incoming AFSK signal. The schematic would include components such as a radio frequency (RF) front end, which consists of an RF amplifier, a mixer for frequency conversion, and an intermediate frequency (IF) filter to eliminate unwanted signals.
The RF amplifier enhances the weak incoming signals before they are mixed with a local oscillator signal in the mixer. This process shifts the frequency of the incoming signal down to a more manageable IF, allowing for better filtering and demodulation. The IF filter is crucial in ensuring that only the desired frequency components reach the demodulator, thereby improving the overall signal-to-noise ratio.
Following the demodulation stage, the output signal is typically processed by a microcontroller or a dedicated decoder chip that interprets the data stream. This component would be programmed to recognize the specific 12-bit activation codes and execute corresponding actions, such as activating or deactivating the bugging device. The microcontroller's firmware may also include routines for entering sleep mode, which conserves battery life by shutting down the RF transit section while keeping the receive section active.
The design anomaly mentioned in the description may relate to the choice of components or circuit layout that could be exploited by TSCM specialists. For instance, if the RF front end is overly sensitive or improperly shielded, it could allow for easier detection of the bugging device during sweeps. Additionally, the simplicity of the frequency inversion scrambling method may make it vulnerable to interception and decoding, providing further opportunities for TSCM professionals to identify and neutralize the device.
In summary, the schematic for the receiver section of the Spectronics bugging device reveals key operational elements and potential vulnerabilities that can be exploited in counter-surveillance efforts. Understanding these components and their interactions is essential for effectively detecting and mitigating the risks posed by such eavesdropping devices.This allows a TSCM specialist the ability to "blink" a Spectronics bugging device on for a second or two to detect it, and then to shut it back down before the eavesdropper catches on to the fact that his bugging device has just been caught. There is a small number of 12 bit "house" activation codes that can be run though in less than a second, bu
t they are only 6-8 in total. If you can`t hit it with the basic sequence then you will have to run though the full 12 bit sequence which will till take you less than ten minutes. The signal is transmitted at 433. 92 MHz as a AFSK data stream so most of you will have no problem getting the bug to give itself up (cracks about Prom dresses not withstanding).
The entire RF TRANSIT section shuts down when these things go into sleep mode, but the RECEIVE section stays awake on monitors the command channel all the time. The bugs are EXTREMELY easy to find them if you can use the bypass codes (less than a second), or the full sequence (less then 10 minutes) due to the small size of the activation key, and known activation frequency.
You can also find these little bugs by purchasing 8 ea car alarm remote (12+ bits) and simply pressing the button of each remote in sequence. You will need to reprogram in each of the remote activation codes into the remote, but your only talking about a sequence that is two bytes long (please stop laughing at such a simple method to find them).
A company called Oregon Scientific and Davis Instruments makes a line of Wireless Digital Thermometers that operate on the same frequency as, use the same bit stream as, and operate similar to these Spectronics Eavesdropping devices. The only problem with these thermometers is that if you have a Spectronics eavesdropping system nearby you run the risk of accidently activating the eavesdropping device during a bug sweep as the weather changes (cough-cough, nudge-nudge, wink-wink).
Hand held code grabbers used by the car alarm and garage door opener industry also make short work out of tracking these devices, but their possession and/or use may cause legal issues. To run through the entire sequence of house command signals you only need to spit out 128 bits of data, or 16 characters.
This is important as you can also use a wireless keyboard that operates at 433. 92 MHz which uses the same format and merely type in the 16 character "all on" sequence via the keyboard, but using the car alarm remote is a little easier. If you end up having to search for all 12 bit variations then you wouldn`t want to use the car alarm method and would need something that could tumble the entire sequence.
Spectronics is not the only company to use either this frequency, nor are they the only ones to use the 12 bit activation code. If you really want to take an eavesdropper to the ground you can issue the same sequence at 310 MHz, and 916 MHz at the same time you were transmitting the 433 MHz codes.
Here is the command structure, so if somebody wants to really play with the remote controls that will need to pulse out the following (it is a four bit command word, in addition to the addresing word of 12 bits). The "scrambling" used by the audio circuit eavesdropping system is simple frequency inversion that many scanners can monitor, or which anybody can decode and listen to on a PC.
Anybody who is in the middle of a bug sweep and who hears the characteristic "Donald Duck" over their TSCM equipment knows that they are on to the trail of a live bug, and they will not sleep for days until they find the thing. Here is a photograph of the actual bugging devices, the physical dimensions of this module is 35 x 23 x 8 mm (just under 1.
5 cubic inches of volume) for the first picture device and 31x19x6. 1 mm for the other pictured devices. Here is a schematic for the receiver section of the bug, any engineering student will notice a serious design anomaly that can be exploited by the TSCM professional to hunt these devices down: 🔗 External reference
The electronic schematic for the receiver section of the Spectronics bugging device is critical for understanding its operation and vulnerabilities. The receiver is typically designed to operate within the 433.92 MHz frequency band, utilizing a superheterodyne architecture to demodulate the incoming AFSK signal. The schematic would include components such as a radio frequency (RF) front end, which consists of an RF amplifier, a mixer for frequency conversion, and an intermediate frequency (IF) filter to eliminate unwanted signals.
The RF amplifier enhances the weak incoming signals before they are mixed with a local oscillator signal in the mixer. This process shifts the frequency of the incoming signal down to a more manageable IF, allowing for better filtering and demodulation. The IF filter is crucial in ensuring that only the desired frequency components reach the demodulator, thereby improving the overall signal-to-noise ratio.
Following the demodulation stage, the output signal is typically processed by a microcontroller or a dedicated decoder chip that interprets the data stream. This component would be programmed to recognize the specific 12-bit activation codes and execute corresponding actions, such as activating or deactivating the bugging device. The microcontroller's firmware may also include routines for entering sleep mode, which conserves battery life by shutting down the RF transit section while keeping the receive section active.
The design anomaly mentioned in the description may relate to the choice of components or circuit layout that could be exploited by TSCM specialists. For instance, if the RF front end is overly sensitive or improperly shielded, it could allow for easier detection of the bugging device during sweeps. Additionally, the simplicity of the frequency inversion scrambling method may make it vulnerable to interception and decoding, providing further opportunities for TSCM professionals to identify and neutralize the device.
In summary, the schematic for the receiver section of the Spectronics bugging device reveals key operational elements and potential vulnerabilities that can be exploited in counter-surveillance efforts. Understanding these components and their interactions is essential for effectively detecting and mitigating the risks posed by such eavesdropping devices.This allows a TSCM specialist the ability to "blink" a Spectronics bugging device on for a second or two to detect it, and then to shut it back down before the eavesdropper catches on to the fact that his bugging device has just been caught. There is a small number of 12 bit "house" activation codes that can be run though in less than a second, bu
t they are only 6-8 in total. If you can`t hit it with the basic sequence then you will have to run though the full 12 bit sequence which will till take you less than ten minutes. The signal is transmitted at 433. 92 MHz as a AFSK data stream so most of you will have no problem getting the bug to give itself up (cracks about Prom dresses not withstanding).
The entire RF TRANSIT section shuts down when these things go into sleep mode, but the RECEIVE section stays awake on monitors the command channel all the time. The bugs are EXTREMELY easy to find them if you can use the bypass codes (less than a second), or the full sequence (less then 10 minutes) due to the small size of the activation key, and known activation frequency.
You can also find these little bugs by purchasing 8 ea car alarm remote (12+ bits) and simply pressing the button of each remote in sequence. You will need to reprogram in each of the remote activation codes into the remote, but your only talking about a sequence that is two bytes long (please stop laughing at such a simple method to find them).
A company called Oregon Scientific and Davis Instruments makes a line of Wireless Digital Thermometers that operate on the same frequency as, use the same bit stream as, and operate similar to these Spectronics Eavesdropping devices. The only problem with these thermometers is that if you have a Spectronics eavesdropping system nearby you run the risk of accidently activating the eavesdropping device during a bug sweep as the weather changes (cough-cough, nudge-nudge, wink-wink).
Hand held code grabbers used by the car alarm and garage door opener industry also make short work out of tracking these devices, but their possession and/or use may cause legal issues. To run through the entire sequence of house command signals you only need to spit out 128 bits of data, or 16 characters.
This is important as you can also use a wireless keyboard that operates at 433. 92 MHz which uses the same format and merely type in the 16 character "all on" sequence via the keyboard, but using the car alarm remote is a little easier. If you end up having to search for all 12 bit variations then you wouldn`t want to use the car alarm method and would need something that could tumble the entire sequence.
Spectronics is not the only company to use either this frequency, nor are they the only ones to use the 12 bit activation code. If you really want to take an eavesdropper to the ground you can issue the same sequence at 310 MHz, and 916 MHz at the same time you were transmitting the 433 MHz codes.
Here is the command structure, so if somebody wants to really play with the remote controls that will need to pulse out the following (it is a four bit command word, in addition to the addresing word of 12 bits). The "scrambling" used by the audio circuit eavesdropping system is simple frequency inversion that many scanners can monitor, or which anybody can decode and listen to on a PC.
Anybody who is in the middle of a bug sweep and who hears the characteristic "Donald Duck" over their TSCM equipment knows that they are on to the trail of a live bug, and they will not sleep for days until they find the thing. Here is a photograph of the actual bugging devices, the physical dimensions of this module is 35 x 23 x 8 mm (just under 1.
5 cubic inches of volume) for the first picture device and 31x19x6. 1 mm for the other pictured devices. Here is a schematic for the receiver section of the bug, any engineering student will notice a serious design anomaly that can be exploited by the TSCM professional to hunt these devices down: 🔗 External reference